Three SSL Client Sockets#
1. Purpose / Scope#
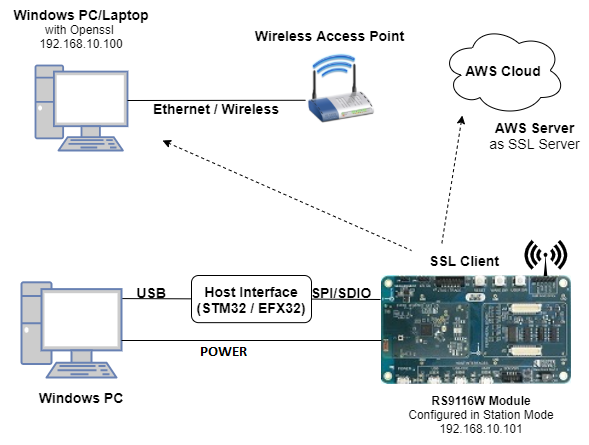
This application demonstrates how RS9116W EVK will connect to three different SSL servers with three different set of SSL certificates and loading certificates into the FLASH.
2. Prerequisites / Setup Requirements#
Before running the application, set up the following:
2.1 Hardware Requirements#
Windows PC with Host interface (UART / SPI/ SDIO).
Silicon Labs RS9116 Wi-Fi Evaluation Kit
Host MCU Eval Kit. This example has been tested with:
Silicon Labs WSTK + EFR32MG21
Silicon Labs WSTK + EFM32GG11
AWS server information like domain name running in the cloud which supports SSL connection.
Wireless Access Point
TCP server over SSL running in Windows PC (This application uses OpenSSL to create TCP server over SSL)

2.2 Software Requirements#
Embedded Development Environment
For STM32, use licensed Keil IDE
For Silicon Labs EFx32, use the latest version of Simplicity Studio
OpenSSL Application in Windows PC (Remote PC).
3. Application Build Environment#
3.1 Platform#
The Application can be built and executed on below Host platforms
3.2 Host Interface#
By default, the application is configured to use the SPI bus for interfacing between Host platforms(STM32F411 Nucleo / EFR32MG21) and the RS9116W EVK.
This application is also configured to use the SDIO bus for interfacing between Host platforms(EFM32GG11) and the RS9116W EVK.
3.3 Project Configuration#
The Application is provided with the project folder containing Keil and Simplicity Studio project files.
Keil Project
The Keil project is used to evaluate the application on STM32.
Project path:
<SDK>/examples/snippets/wlan/three_ssl_concurrent_client_sockets/projects/three_ssl_concurrent_client_sockets-nucleo-f411re.uvprojx
Simplicity Studio
The Simplicity Studio project is used to evaluate the application on EFR32MG21.
Project path:
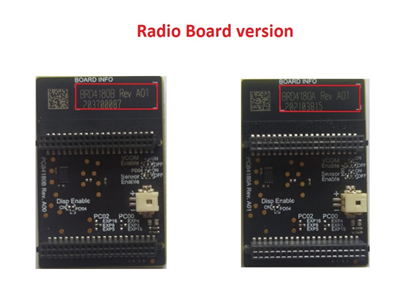
If the Radio Board is BRD4180A or BRD4181A, then access the path
<SDK>/examples/snippets/wlan/three_ssl_concurrent_client_sockets/projects/three_ssl_concurrent_client_sockets-brd4180a-mg21.slsprojIf the Radio Board is BRD4180B or BRD4181B, then access the path
<SDK>/examples/snippets/wlan/three_ssl_concurrent_client_sockets/projects/three_ssl_concurrent_client_sockets-brd4180b-mg21.slsprojUser can find the Radio Board version as given below

EFM32GG11 platform
The Simplicity Studio project is used to evaluate the application on EFM32GG11.
Project path:
<SDK>/examples/snippets/wlan/station_ping/projects/station_ping-brd2204a-gg11.slsproj
3.4 Bare Metal/RTOS Support#
This application supports bare metal and RTOS environment. By default, the application project files (Keil and Simplicity studio) are provided with bare metal configuration in the SDK.
4. Application Configuration Parameters#
The application can be configured to suit user requirements and development environment. Read through the following sections and make any changes needed.
4.1 Open rsi_three_ssl_client_sockets.c file#
4.1.1 User must update the below parameters#
SSID refers to the name of the Access point.
#define SSID "SILABS_AP"SECURITY_TYPE refers to the type of security. In this application STA supports Open, WPA-PSK, WPA2-PSK securities.
Valid configuration is:
RSI_OPEN - For OPEN security mode
RSI_WPA - For WPA security mode
RSI_WPA2 - For WPA2 security mode
#define SECURITY_TYPE RSI_WPA2PSK refers to the secret key if the Access point configured in WPA-PSK /WPA2-PSK security modes.
#define PSK "1234567890"DEVICE_PORT1 port refers TCP client port number
#define DEVICE_PORT1 <local port>SERVER_PORT1 port refers remote TCP server port number which is opened in remote peer/ which is running on cloud.
#define SERVER_PORT1 <remote port>DEVICE_PORT2 refers another TCP client port number
#define DEVICE_PORT2 <local port>SERVER_PORT2 port refers another remote TCP server port number which is opened in remote peer/ which is running on cloud.
#define SERVER_PORT2 <remote port>DEVICE_PORT3 refers another TCP client port number
#define DEVICE_PORT3 <local port>SERVER_PORT3 port refers another remote TCP server port number which is opened in remote peer/ which is running on cloud.
#define SERVER_PORT3 <remote port>SERVER_IP_ADDRESS refers remote peer IP address to connect with TCP server socket over SSL running on the Windows PC.
#define SERVER_ADDR 0x640AA8C0IP address should be in long format and in little endian byte order.
Example: To configure "192.168.10.100" as IP address, update the macro DEVICE_IP as 0x640AA8C0.
Note: For Servers running on cloud, get the IP using DNS server.
4.1.2 The desired parameters are provided below. User can also modify the parameters as per their needs and requirements.#
The following parameters are configured if OS is used. WLAN task should be of low priority
#define RSI_WLAN_TASK_PRIORITY 1Driver task should have the highest priority among all threads
#define RSI_DRIVER_TASK_PRIORITY 2WLAN Task stack size is configured by this macro
#define RSI_WLAN_TASK_STACK_SIZE 500Driver Task stack size is configured by this macro
#define RSI_DRIVER_TASK_STACK_SIZE 500Application memory length which is required by the driver
#define GLOBAL_BUFF_LEN 15000RSI_SSL_BIT_ENABLE
0 - Disable SSL bitmap 1 - Enable SSL bitmap This bit should be enabled for SSL connection
#define RSI_SSL_BIT_ENABLE 1Note: If certificates are not there in flash, then ssl handshake will fail.
DHCP_MODE refers whether IP address configured through DHCP or STATIC
#define DHCP_MODE 1Note: If user wants to configure STA IP address through DHCP then set DHCP_MODE to "1" and skip configuring the following DEVICE_IP, GATEWAY and NETMASK macros. (Or) If user wants to configure STA IP address through STATIC then set DHCP_MODE macro to "0" and configure following DEVICE_IP, GATEWAY and NETMASK macros.
IP address to be configured to the device in STA mode should be in long format and in little endian byte order.
Example: To configure "192.168.10.10" as IP address, update the macro DEVICE_IP as 0x0A0AA8C0.
#define DEVICE_IP 0X0A0AA8C0IP address of the gateway should also be in long format and in little endian byte order.
Example: To configure "192.168.10.1" as Gateway, update the macro GATEWAY as 0x010AA8C0.
#define GATEWAY 0x010AA8C0IP address of the network mask should also be in long format and in little endian byte order.
Example: To configure "255.255.255.0" as network mask, update the macro NETMASK as 0x00FFFFFF.
#define NETMASK 0x00FFFFFFAWS_DOMAIN_NAME refers to domain name of the AWS server
#define AWS_DOMAIN_NAME "a25jwtlmds8eip-ats.iot.us-east-2.amazonaws.com"4.2 Open rsi_wlan_config.h file. User can also modify the below parameters as per their needs and requirements.#
#define CONCURRENT_MODE RSI_DISABLE
#define RSI_FEATURE_BIT_MAP FEAT_SECURITY_OPEN
#define RSI_TCP_IP_BYPASS RSI_DISABLE
#define RSI_TCP_IP_FEATURE_BIT_MAP (TCP_IP_FEAT_DHCPV4_CLIENT | TCP_IP_FEAT_SSL | TCP_IP_FEAT_DNS_CLIENT | TCP_IP_FEAT_EXTENSION_VALID)
#define RSI_EXT_TCPIP_FEATURE_BITMAP EXT_TCP_IP_FEAT_SSL_THREE_SOCKETS
#define RSI_CUSTOM_FEATURE_BIT_MAP FEAT_CUSTOM_FEAT_EXTENTION_VALID
#define RSI_EXT_CUSTOM_FEATURE_BIT_MAP RAM_LEVEL_NWP_ALL_MCU_ZERO
#define RSI_BAND RSI_BAND_2P4GHZPower save configuration
By default, the application is configured without power save.
#define ENABLE_POWER_SAVE 0If user wants to run the application in power save, modify the below macro.
#define ENABLE_POWER_SAVE 14.3 Setting up Security Certificates#
To authenticate and securely connect with AWS, your Wi-Fi device requires a unique x.509 security certificate and private key, as well as a CA certificate which is used to verify the AWS server. Security credentials need to be converted into a C-array rather than PEM format provided by AWS; they also need to be added to your project.
The WiSeConnect SDK includes a Python 3 script to streamline the conversion process. This script certificate_to_array.py is in the SDK 'resources' directory certificate_to_array.py.
To convert the device certificate and private key to C arrays, open a system command prompt and use the script as indicated in the following examples.
$> python3 certificate_to_array.py <input filename> <output arrayname>
For example:
$> python3 certificate_to_array.py d8f3a44d3f.cert.pem aws_client_certificate
$> python3 certificate_to_array.py d8f3a44d3f.private.key aws_client_private_certificateAfter running the script on the certificate and private key, two new files are created.
aws_client_certificate.pem.crt.h
aws_client_private_key.pem.key.hCopy the two files aws_client_certificate.pem.crt.h and aws_client_private_key.pem.key.h to the WiSeConnect directory: /resources/certificates, overwriting any existing files with same name.
The Root CA certificate used by your Wi-Fi device to verify the AWS server is already included in the WiSeConnect SDK; no additional setup is required. For reference, Amazon uses Starfield Technologies to secure the AWS website, the WiSeConnect SDK includes the Starfield CA Certificate.
NOTE : For AWS connectivity, StarField Root CA Class 2 certificate has the highest authority being at the top of the signing hierarchy.
The StarField Root CA Class 2 certificate is an expected/required certificate which usually comes pre-installed in the operating systems and it plays a key part in certificate chain verification when a device is performing TLS authentication with the IoT endpoint.
On RS9116 device, we do not maintain root CA trust repository due to memory constraints, so it is mandatory to load StarField Root CA Class 2 certificate for successful connection to AWS server.
The certificate chain sent by AWS server is as below: id-at-commonName=Amazon,id-at-organizationalUnitName=Server CA 1B,id-at-organizationName=Amazon,id-at-countryName=US id-at-commonName=Amazon Root CA 1,id-at-organizationName=Amazon,id-at-countryName=US id-at-commonName=Starfield Services Root Certificate Authority ,id-at-organizationName=Starfield Technologies, Inc.,id-at-localityName=Scottsdale,id-at- stateOrProvinceName=Arizona,id-at-countryName=US)
On RS9116, to authenticate the AWS server, first validate the Root CA received with the Root CA loaded on the device. Once the Root CA validation is successful, other certificates sent from the AWS server are validated. RS9116 do not authenticate to the AWS server if intermediate CA certificates are loaded instead of StarField Root CA Class 2 certificate and will result in Handshake error. StarField Root CA Class 2 certificate is at https://certs.secureserver.net/repository/sf-class2-root.crt
Reference links : https://aws.amazon.com/blogs/security/how-to-prepare-for-aws-move-to-its-own-certificate-authority/
5. Testing the Application#
User has to follow the below steps for the successful execution of the application.
5.1 Loading the RS9116W Firmware#
Refer Getting started with a PC to load the firmware into RS9116W EVK. The firmware file is located in <SDK>/firmware/
5.2 Building the Application on the Host Platform#
5.2.1 Using STM32#
Refer Getting started with STM32
Open the project
<SDK>/examples/snippets/wlan/three_ssl_concurrent_client_sockets/projects/three_ssl_concurrent_client_sockets-nucleo-f411re.uvprojxBuild and Debug the project
Check for the RESET pin:
If RESET pin is connected from STM32 to RS9116W EVK, then user need not press the RESET button on RS9116W EVK before free run.
If RESET pin is not connected from STM32 to RS9116W EVK, then user need to press the RESET button on RS9116W EVK before free run.
Free run the project
Then continue the common steps from 5.3
5.2.2 Using EFX32#
Refer Getting started with EFX32, for settin-up EFR & EFM host platforms
Open Simplicity Studio and import the EFR32/EFM32 project from
<SDK>/examples/snippets/wlan/three_ssl_concurrent_client_sockets/projectsSelect the appropriate .slsproj as per Radio Board type mentioned in Section 3.3 for EFR32 board. (or)
Select the *.brd2204a-gg11.slsproj for EFM32GG11 board.
Compile and flash the project in to Host MCU
Debug the project
Check for the RESET pin:
If RESET pin is connected from EFX32 to RS9116W EVK, then user need not press the RESET button on RS9116W EVK before free run
If RESET pin is not connected from EFX32 to RS9116W EVK, then user need to press the RESET button on RS9116W EVK before free run
Free run the project
Then continue the common steps from 5.3
5.3 Common Steps#
Configure the Access point in OPEN / WPA-PSK / WPA2-PSK mode to connect RS9116W EVK in STA mode.
Copy the certificates server-cert and server-key into Openssl/bin folder in the Windows PC (Remote PC).
Note: All the certificates are given in the SDK. Path:
<SDK>/resources/certificates
In Windows PC (Remote PC) which is connected to AP, run the Openssl server by giving the following command
Openssl.exe s_server -accept<SERVER_PORT> -cert <server_certificate_file_path> -key <server_key_file_path> -tls<tls_version> Example: openssl.exe s_server -accept 5001 -cert server-cert.pem -key server-key.pem -tls1
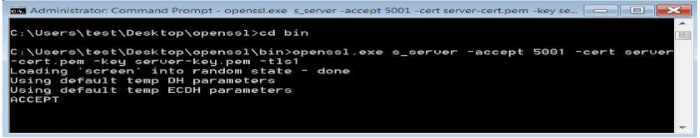

Make sure the SSL server is running in the cloud (check with the domain name).
After the program gets executed, RS9116W EVK would be connected to Access point having the configuration same that of in the application and get IP.
The Device which is configured as SSL client will connect to three different remote SSL servers.
Appendix#
Create an AWS Thing#
Create a thing in the AWS IoT registry to represent your IoT Device.
In the AWS IoT console, in the navigation pane, under Manage, choose All devices, and then choose Things.

If a You don't have any things yet dialog box is displayed, choose Register a thing. Otherwise, choose Create.
Click on Create things.
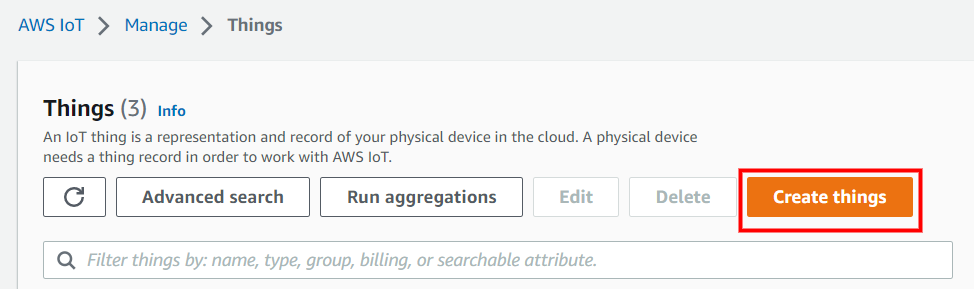

On the Create things page, choose Create a single thing and click next.
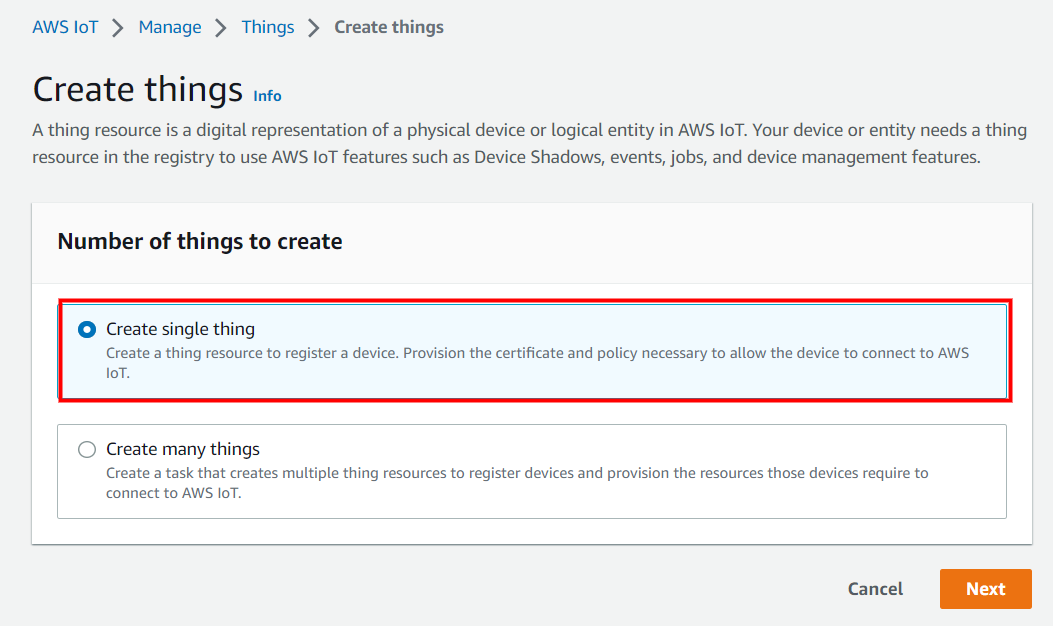

On the Specify thing properties page, enter a name for your IoT thing (for example, Test_IoT), and choose Unnamed shadow (classic) in the Device Shadow section, then choose Next. You can't change the name of a thing after you create it. To change a thing's name, you must create a new thing, give it the new name, and then delete the old thing.
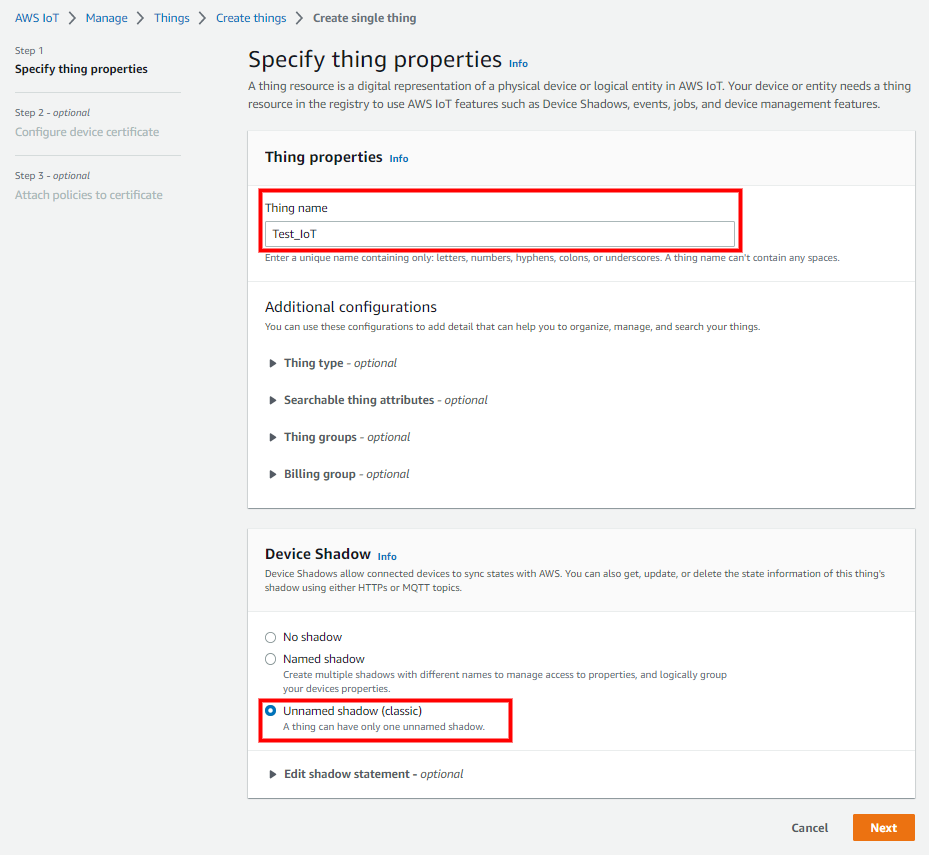

During the Configure device certificate step, choose Auto-generate a new certificate (recommended) option and click next.
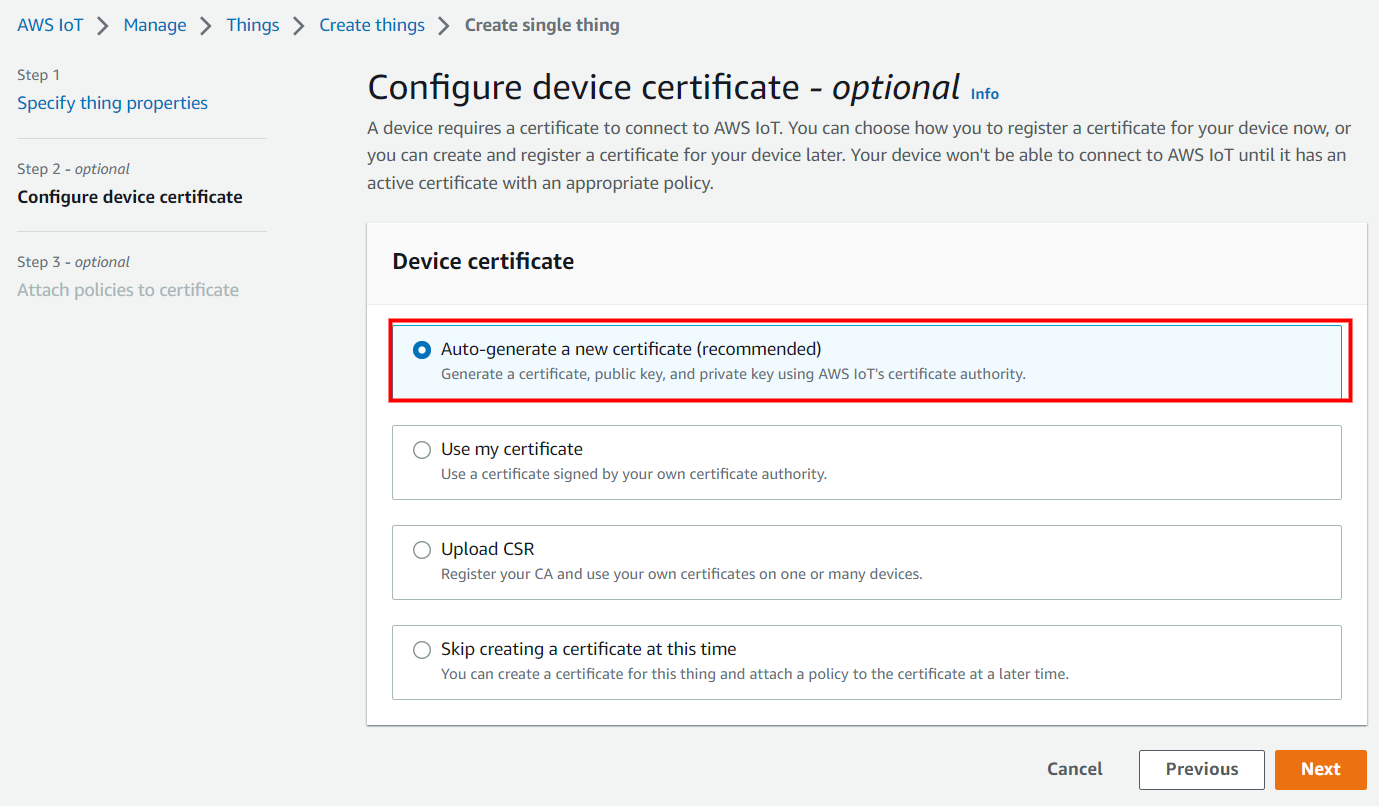

Attach the policy to the thing created.
If you have any existing policy, attach it and click on create thing.
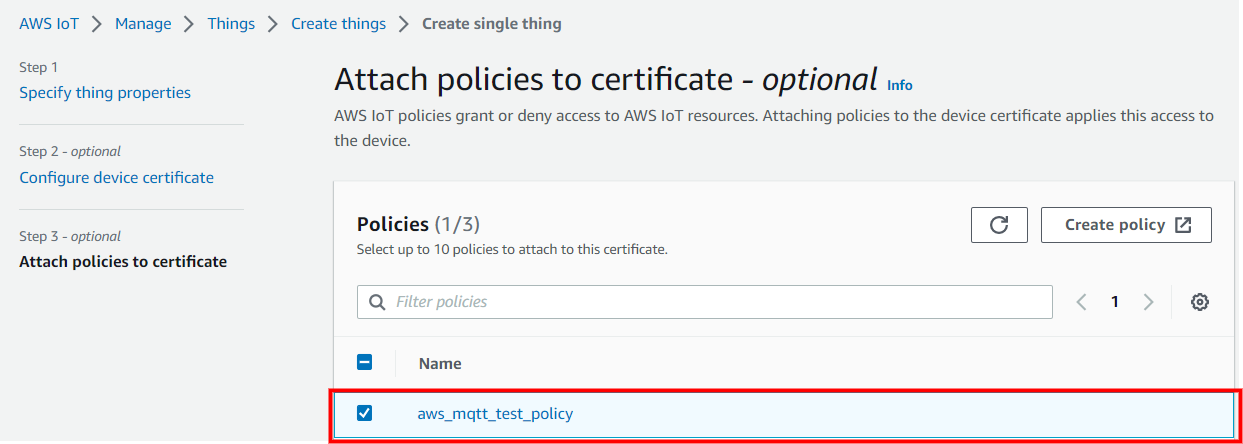

If the policy is not yet created, follow the below steps.
Choose Create policy and fill the fields as per your requirements.

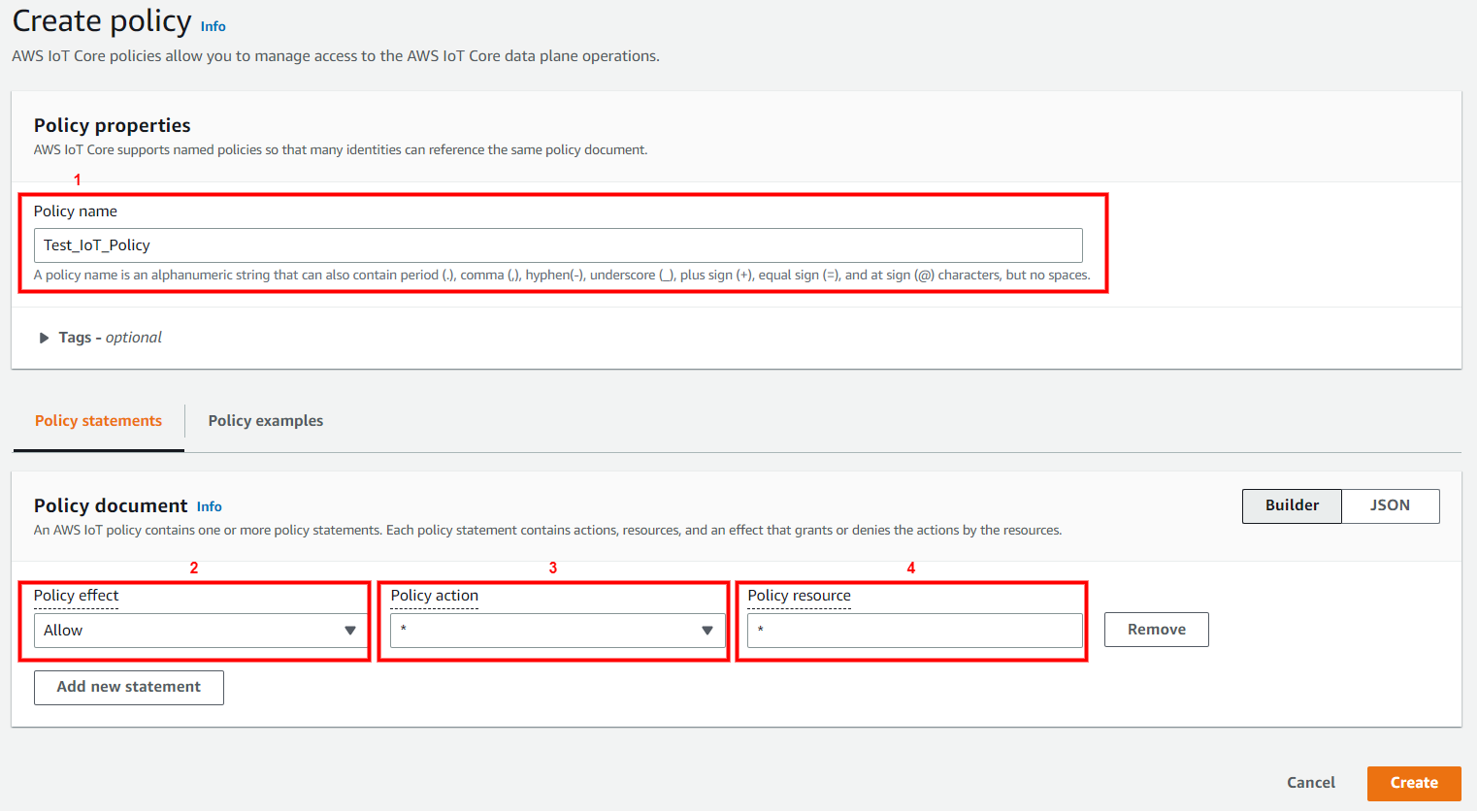
Give the Name to your Policy, and fill the Action and Resource ARN fields as shown in the below image. Click on Allow under Effect and click Create.

Choose the created policy and click on Create thing.
Choose the Download links to download the device certificate, private key, and root CA certificate. Root CA certificate is already present in SDK (aws_starfield_ca.pem.h), and can be directly used.
Warning: This is the only instance you can download your device certificate and private key. Make sure to save them safely.
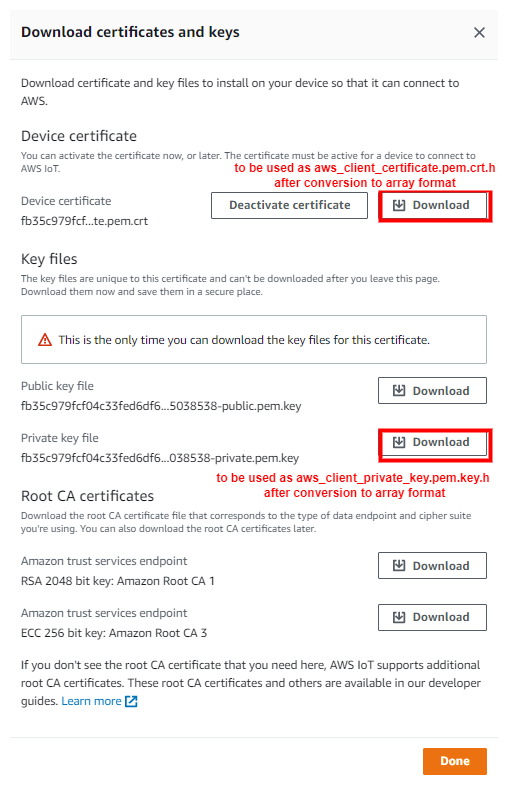

Click Done.
The created thing now should be visible on the AWS console (Manage > All devices > Things).
Appendix: Steps to create a policy from AWS console#
Navigate to AWS IoT console
Choose Policies under Secure


Click on Create

Compressed Debug Logging#
To enable the compressed debug logging feature please refer to Logging User Guide
