EAP Methods#
EAP methods are specific authentication mechanisms used within the EAP framework to facilitate the authentication process between a supplicant and an authentication server. These methods define how authentication credentials are exchanged and verified during the EAP authentication process. Here are the EAP methods supported by SiWN917.
EAP TLS - EAP Transport Layer Protocol#
EAP-TLS utilizes mutual authentication and digital certificates to establish a secure TLS-encrypted tunnel between the supplicant and the authentication server. It is considered highly secure and is widely used in enterprise environments that require strong authentication.
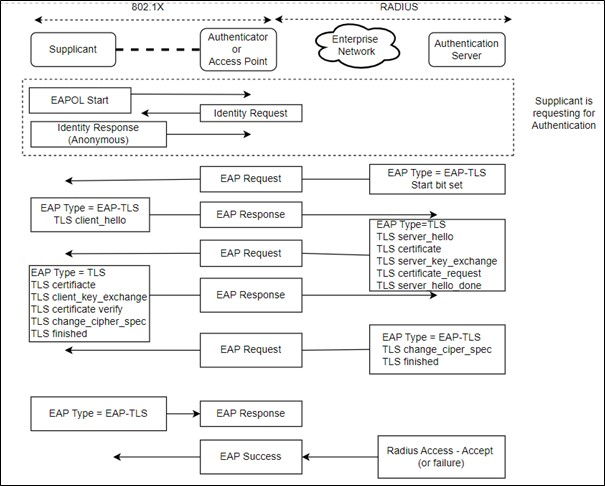
The supplicant sends an EAPOL-Start message to the access point (AP) to initiate the EAP authentication process.
The EAP server must respond with EAP Request/Identity message to the supplicant with EAP-Type set to EAP-TLS, the Start(S) bit is set (True) and without any data and asks the supplicants to provide its identity.
The supplicant then sends an EAP-Response packet with EAP-Type to EAP-TLS, containing a TLS client_hello along with the cipher suites supported, in the handshake message.
The EAP server, then responds with a handshake message – server_hello (with the cipher suite picked and supported), TLS certificate, server_key_exchange, certificate_request, server_hello_done.
The Client must respond to the EAP-Request with an EAP-Response packet of EAP-Type set to EAP-TLS. And the authentication server starts verifying the data sent by supplicant like TLS certificate verify, TLS client_key_exchange, change_cipher_spec.
If a ChangeCipherSpec message is sent by the client and the server responds with its own ChangeCipherSpec message to confirm the change to new Cipher Spec.
If the EAP server authenticates successfully, the peer must send an EAP-Response packet of EAP-Type to EAP-TLS
The EAP server then responds with an EAP-Success message.

Configuring SiWN917 in EAP-TLS#
To configure SiWN917 in EAP-TLS, follow the steps below:
Change the security type to SL_WIFI_WPA2_ENTERPRISE. Supported Enterprise client securities are:
WPA-EAP: SL_WIFI_WPA_ENTERPRISE
WPA2-EAP: SL_WIFI_WPA2_ENTERPRISE
Change the encryption type to SL_WIFI_EAP_TLS_ENCRYPTION.
Mostly, EAP-TLS method uses root CA certificate and public-private key pairs for authentication.
Note: To know more about loading certificates, and other configurations, refer to the readme.
EAP TTLS - EAP Tunneled Transport Layer Security#
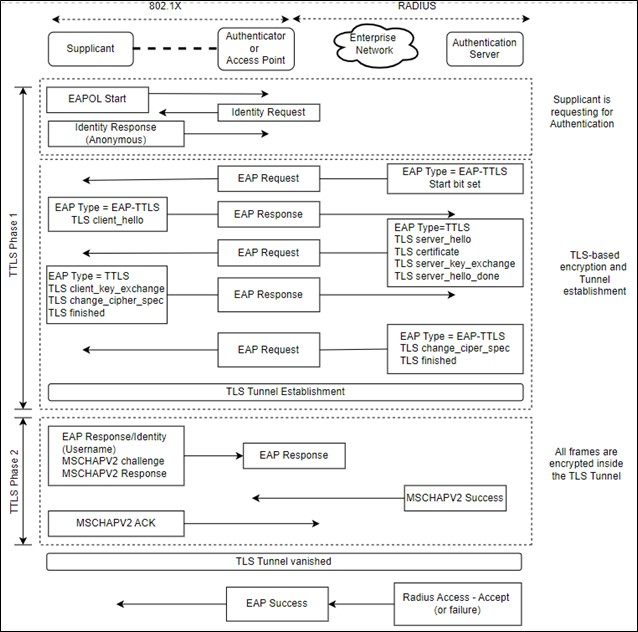
EAP-TTLS was developed as an extension of the EAP-TLS (Transport Layer Security) protocol. It provides a way to secure the authentication process while still using existing username and password-based authentication mechanisms. In EAP-TTLS, the authentication process is divided into two phases, the tunnel establishment phase and the authentication phase.
Tunnel Establishment: This phase sets up a secure tunnel between the client and the authentication server using Transport Layer Security (TLS) to provide encryption and integrity protection. And this phase protects the subsequent authentication process within the tunnel, including the exchange of credentials.
Authentication: Once the secure tunnel is established, the client sends its credentials (typically a username and password) to the authentication server. The server authorizes client access based on the authentication and authorization results. If successful, the authentication process ends and provides a successful connection.

Configuring SiWN917 in EAP-TTLS#
To configure SiWN917 in EAP-TLS, follow the steps below
Change the security type to SL_WIFI_WPA2_ENTERPRISE. Supported Enterprise client securities are:
WPA-EAP: SL_WIFI_WPA_ENTERPRISE
WPA2-EAP: SL_WIFI_WPA2_ENTERPRISE
Change the encryption type to SL_WIFI_EAP_TTLS_ENCRYPTION.
Note: To know more about loading certificates, and other configurations, refer to the readme.
EAP PEAP - EAP Protected Extensible Authentication Protocol#
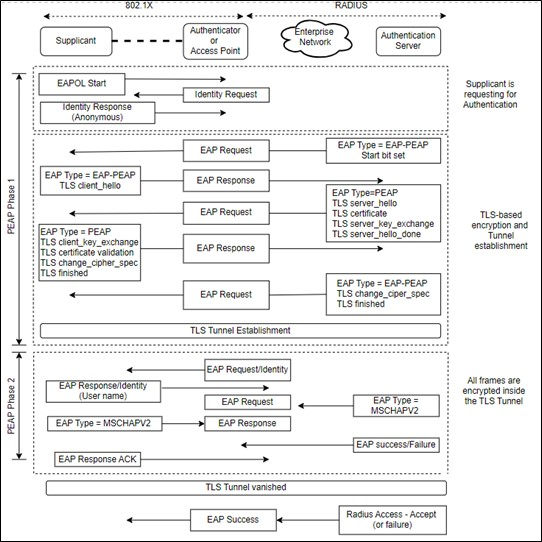
The Protected Extensible Authentication Protocol, also known as Protected EAP or simply PEAP, is a protocol that encapsulates the Extensible Authentication Protocol (EAP) within an encrypted and authenticated Transport Layer Security (TLS) tunnel.
PEAP is similar to EAP-TTLS in design, requiring only a server-side certificate to create a secure TLS tunnel to protect user authentication, and uses server-side public key certificates to authenticate the server. It then creates an encrypted TLS tunnel between the client and the authentication server. The tunnel method is also referred to as the "inner method" and provides user authentication.

Configuring SiWN917 in EAP-PEAP#
To configure SiWN917 in EAP-TLS, follow the steps below:
Change the security type to SL_WIFI_WPA2_ENTERPRISE. Supported Enterprise client securities are:
WPA-EAP: SL_WIFI_WPA_ENTERPRISE
WPA2-EAP: SL_WIFI_WPA2_ENTERPRISE
Change the encryption type to SL_WIFI_PEAP_MSCHAPV2_ENCRYPTIONS.
Supported inner method in SiWN917 is MSCHAPV2.
Note: To know more about loading certificates, and other configurations, refer to the readme.
EAP FAST - EAP Flexible Authentication via Secure Tunneling#
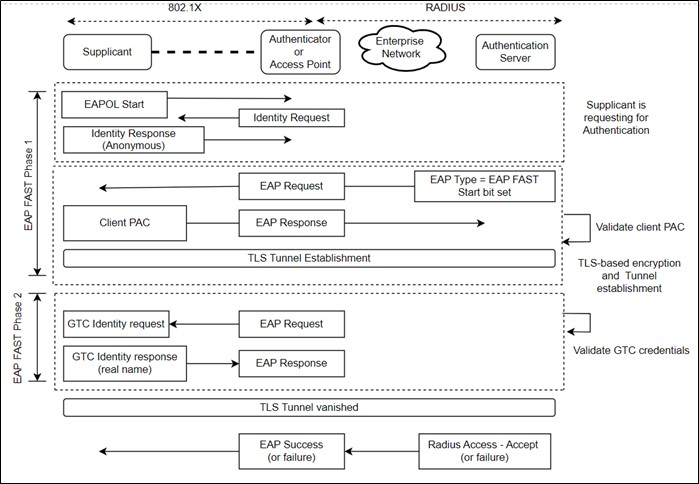
In EAP FAST, use of server certificates is optional and uses a Protected Access Credential (PAC) to establish a TLS tunnel in which client credentials are verified and ensure a secure connection. These PAC files can be provisioned either AUTO or MANUAL.
Auto Provisioning (PAC file is not required)
Manual Provisioning (PAC file is required)
Provisioning#
1. Auto Provisioning#
The connection between the AP and the client is done without loading the PAC file into the Client. And this can be done in 2 ways,
Internal Radius server: Some Access Points have this feature, configure the Access Point in the Enterprise mode by selecting an option for the Internal radius server and add a WLAN user with the username, password, and Shared secret. Configure the client in EAP-FAST and enter the username and Password as mentioned in the Access Point.
External Radius server: There is no specific Access Point required here, Any Access Point supporting EAP can be used. Configure the radius server for EAP-FAST and add the IP address of the PC running the radius server in Access Point settings. Configure the client in EAP-FAST and enter the username and Password as mentioned in the radius server.
2. Manual Provisioning#
The connection between the AP and the client is done only when the PAC file is loaded into the Client.
This can be done by using both internal and external radius servers. Any Access Point supporting EAP can be used. Configure the radius server for EAP-FAST and add the IP address of the PC running the radius server in AP settings. Configure the client in EAP-FAST, load the PAC file and enter the username and Password as mentioned in the radius server.

Configuring SiWN917 in EAP-FAST#
To configure SiWN917 in EAP-FAST, follow the steps below:
Change the security type to SL_WIFI_WPA2_ENTERPRISE. Supported Enterprise client securities are,
WPA-EAP: SL_WIFI_WPA_ENTERPRISE
WPA2-EAP: SL_WIFI_WPA2_ENTERPRISE
Change the encryption type to SL_WIFI_EAP_FAST_ENCRYPTION.
Note: To know more about loading certificates, and other configurations, refer to the readme.
