Concepts#
Network Layer Security#
This section describes how Zigbee implements security at the network layer, which applies to standard security. Network security provides security independent of the applications that may be running on a Zigbee node. All Zigbee-certified devices must use network layer security. It provides the basic access control for controlling what nodes are allowed to participate in a particular Zigbee network. For application-controlled security, see APS Layer Security.
The Network Key#
Network security uses a network-wide key for encryption and decryption. All devices that are authorized to join the network have a copy of the key and use it to encrypt and decrypt all network messages. The network key also has a sequence number associated with it to identify a particular instance of the key. When the network key is updated, the sequence number is incremented to allow devices to identify which instance of the network key has been used to secure the packet data. The sequence number ranges from 0 to 255. When the sequence number reaches 255, it wraps back to 0.
Note: All Zigbee keys are 128-bits in length.
All devices that are part of a secured Zigbee network have a copy of the network key. It is important for devices in possession of the network key to store it securely. A leak of the network key may impact the confidentiality, integrity, and availability of the entire network.
Hop-by-Hop Security#
It is important to note that network security in Zigbee is done on a hop-by-hop basis. Each router that relays an encrypted packet first verifies that it is a valid encrypted packet before any more processing is done. A router authenticates the packet by executing the Zigbee decryption mechanism and verifying the packet integrity. It then re-encrypts the packet with its own network parameters (such as source address and frame counter) before sending the message to the next hop. Without this protection, an attacker could replay a message into the network that would be routed through several devices, thereby consuming network resources. Using hop-by-hop security allows a router to block attempts to inject bad traffic into the network.
Packet Security#
A packet secured at the network layer is composed of the elements shown in the following figure.
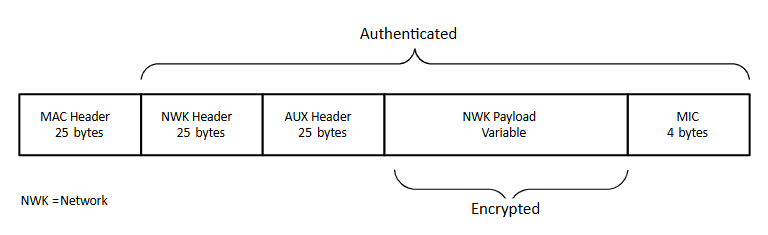

Auxiliary Header#
The auxiliary header contains data about the security of the packet that a receiving node uses to correctly authenticate and decrypt the packet. This data includes the type of key used, the sequence number (if it is the network key), the IEEE address of the device that secured the data, and the frame counter.
Authentication and Encryption#
Zigbee uses a 128-bit symmetric key to encrypt all transmissions at the network layer using AES-128. The network and auxiliary headers are sent in the clear but authenticated, while the network payload is authenticated and encrypted. AES-128 is used to create a hash of the entire network portion of the message (header and payload), which is appended to the end of the message. This hash is known as the Message Integrity Code (MIC) and is used to authenticate the message by insuring it has not been modified. A receiving device hashes the message and verifies the calculated MIC against the value appended to the message. Alterations to the message invalidate the MIC and the receiving node will discard the message entirely.
Note: Zigbee uses a 4-byte MIC.
The Network Security Frame Counter#
A frame counter is included in the auxiliary headers as a means of protecting against replay attacks. All devices have their own outgoing frame counter and they maintain a list of their neighbor's and children's frame counters. Every time a device sends a packet, it increments its outgoing frame counter. A receiving device verifies that the frame counter of the sending device has increased from the last value that it saw. If it has not increased, the packet is silently discarded. If the receiving device is not the final destination, the packet is decrypted and modified to include the routing device's frame counter. The packet is then re-encrypted and sent along to the next hop. As of Zigbee Compliant Platform Revision 23 (R23), security frame counters are synchronized within a network to defend against replay attacks.
The frame counter is 32 bits and may not wrap to zero. The network key can be updated before the frame counter reaches its maximum value. When that occurs, the frame counter may be reset to zero if the local device’s value is above 0x80000000.
Unencrypted Network Data#
All normal network datagrams are required to have network security and a valid frame counter. The only exception is during joining, when devices do not yet have the network key. In that case a joining device's messages are relayed through its parent until it is fully joined and authenticated. Any other messages that are received without network layer security are silently discarded.
Trust Center Networks#
Authentication in a secure network may be controlled by means of a central authority known as a trust center. All devices entering the network are temporarily joined to the network until the trust center is contacted and decides whether or not to allow the new device into the network. The parent of the newly joined device acts as a relay between the trust center and the joining device. Only authentication messages can be sent to or from the device until it is fully joined and authenticated.
The trust center has the option of doing one of three things when a device joins:
Send a copy of the current network key, which the parent relays to the joining device.
Send the parent a command to remove the device from the network, thereby disallowing it from joining.
Ignore the request. Parents will silently remove the device from the network if it does not receive a network key within 2 seconds.
Once the node has the network key, it is considered fully joined and authenticated, and may communicate with any device on the network.
A network operating with a trust center always needs a trust center to authenticate any new devices. Normal messages between two devices do not require the trust center to get involved.
Distributed Trust Center Networks#
Networks may be formed without a centralized authentication. These networks are called Distributed Trust Center Networks. In this case, any router may authorize and authenticate new devices that wish to join.
These networks offer a simpler mechanism for adding devices to the network at the slight expense of a less secure network.
The decision to use a Distributed Trust Center Network or a Trust Center Network is done at the time the network is formed. There is no way to change this decision after the network has been started.
APS Layer Security#
This section describes how Zigbee implements security at the Application Support (APS) layer.
End-to-End Security#
APS security is intended to provide a way to send messages securely within a Zigbee network such that no other device can decrypt the data except the source and destination. This is different than network security, which provides only hop-by-hop security. In that case every device that is part of the network and hears the packet being relayed to its destination and decrypts it.
APS security uses a shared key that only the source and destination know about, thus providing end-to-end security.
Both APS layer and network layer encryption can be used simultaneously to encrypt the contents of a message. In that case APS layer security is applied first, and then network layer security.
A packet secured at the APS Layer is composed of the elements shown in the following figure.
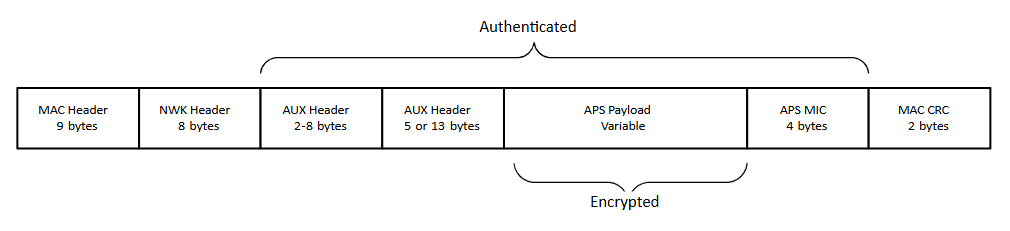

Link Keys#
APS security uses a peer-to-peer key known as the link key. Both devices must have already established this key with one another before sending APS-secured data. There are two types of link keys: trust center link keys and application link keys.
Trust Center Link Keys
The trust center link key is a special link key in which one of the partner devices is the trust center. The stack uses this key to send and receive APS command messages to and from the trust center. The application may also use this key to send APS-encrypted data messages.
All devices in a Zigbee network must have link keys. In a Trust Center Network, the devices must have a Trust Center Link Key. In a Distributed Trust Center Network, this key is called a Distributed Trust Center link key.
Application Link Keys
Application link keys are shared keys that may be established between any two nodes in the network, where neither device is a trust center. They may be used to add additional security to messages being sent to or from the application running on a node. Devices can have a different application link key for each device with which they communicate.
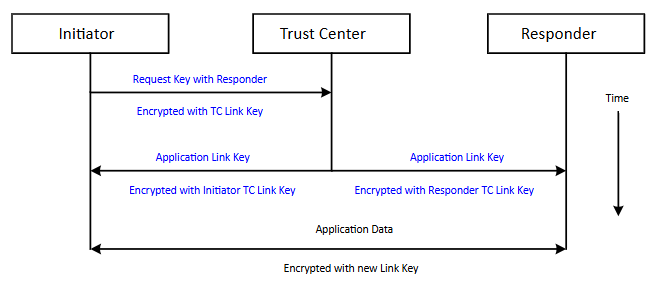
A device may preconfigure an application link key or request a link key between itself and another device. In the latter case it issues a request to the trust center encrypted with its trust center link key. The trust center acts as a trusted third party to both devices, so they can securely establish communications with one another. This is discussed further in section Application Link Keys. The process for establishing an application link key is illustrated in the following figure.

Unencrypted APS Data#
APS layer security operates independently of network layer security. It is required for certain security messages (APS commands) sent to and from the trust center by the Zigbee stack.
Unlike network security, APS security for application messages is optional. Application messages are not automatically encrypted at the APS layer and are not ignored on the receiving side if they do not have APS encryption. Individual applications may choose whether to accept or reject messages that do not have APS layer security. For example, the Smart Energy profile describes what Zigbee Cluster messages are required to have security.
