Debug Lock#
Overview#
The debug access port connected to the Series 2 device's Cortex-M33 processor can be closed by issuing commands to the SE, either from a debugger over DCI or through the mailbox interface. These three debug lock properties govern the behavior of the debug lock.
| Property | Description If Set | Default Value |
|---|---|---|
Debug Lock | The debug port is kept locked on boot. | False (Disabled) |
Device Erase | The Erase Device command is available. | True (Enabled) |
Secure Debug | Secure debug unlock is available. | False (Disabled) |
The following sections describe how to interact with these properties and how to enable debug locks using the SE command interface either over DCI or the mailbox interface. The status of the debug lock can be inspected using the Read Lock Status command.
Standard Debug Unlock#
The device is in standard debug unlock state if the debug lock properties are in default values.
| Secure Debug | Device Erase | Debug Lock | Description |
|---|---|---|---|
Disabled | Enabled | Disabled (Unlock) | All debug operations are allowed. |
Standard Debug Lock#
With the default properties in the table above, the device can be locked using the Apply Lock command. The typical flow for this configuration is simply to issue the Apply Lock command after the device has been programmed, either using a DCI command from the programming debugger or through the mailbox interface.
| Secure Debug | Device Erase | Debug Lock | Description |
|---|---|---|---|
Disabled | Enabled | Enabled (Standard) | The Erase Device command will wipe the main flash and RAM, and then a reset will yield an unlocked device. |
The standard debug lock behaves similarly to Series 1 devices. The access port can be closed, but issuing a device erase wipes the device and opens the debug port again.
Permanent Debug Lock#
The Erase Device command can be disabled, which permanently enables the debug lock. This can be done at any time by issuing the Disable Device Erase command, even after the debug lock has been enabled.
| Secure Debug | Device Erase | Debug Lock | Description |
|---|---|---|---|
Disabled | Disabled | Enabled (Permanent) | The part cannot be unlocked. Devices with Permanent Debug Lock engaged cannot be returned for failure analysis. |
Secure Debug Lock#
For secure debug lock, the debug interface can be temporarily enabled by answering a challenge if the Secure debug property is enabled before locking.
| Secure Debug | Device Erase | Debug Lock | Description |
|---|---|---|---|
Enabled (1) | Disabled (2) | Enabled (Secure) | Secure debug unlock is enabled, which makes it possible to securely open the debug lock temporarily to reprogram or debug a locked device. |
Note:
Secure debug is enabled in two steps before the debug lock is enabled:
a. Install the Public Command Key using Simplicity Studio or Simplicity Commander or directly through the SE Manager API.
b. Enable secure debug using Simplicity Studio or Simplicity Commander or directly through the SE Manager API.
Disable the device erase using Simplicity Studio or Simplicity Commander or directly through the SE Manager API. This is an IRREVERSIBLE action and should be disabled AFTER the secure debug is enabled.
Debug Lock State Transition#
The following figure describes the transitions between different debug lock states.
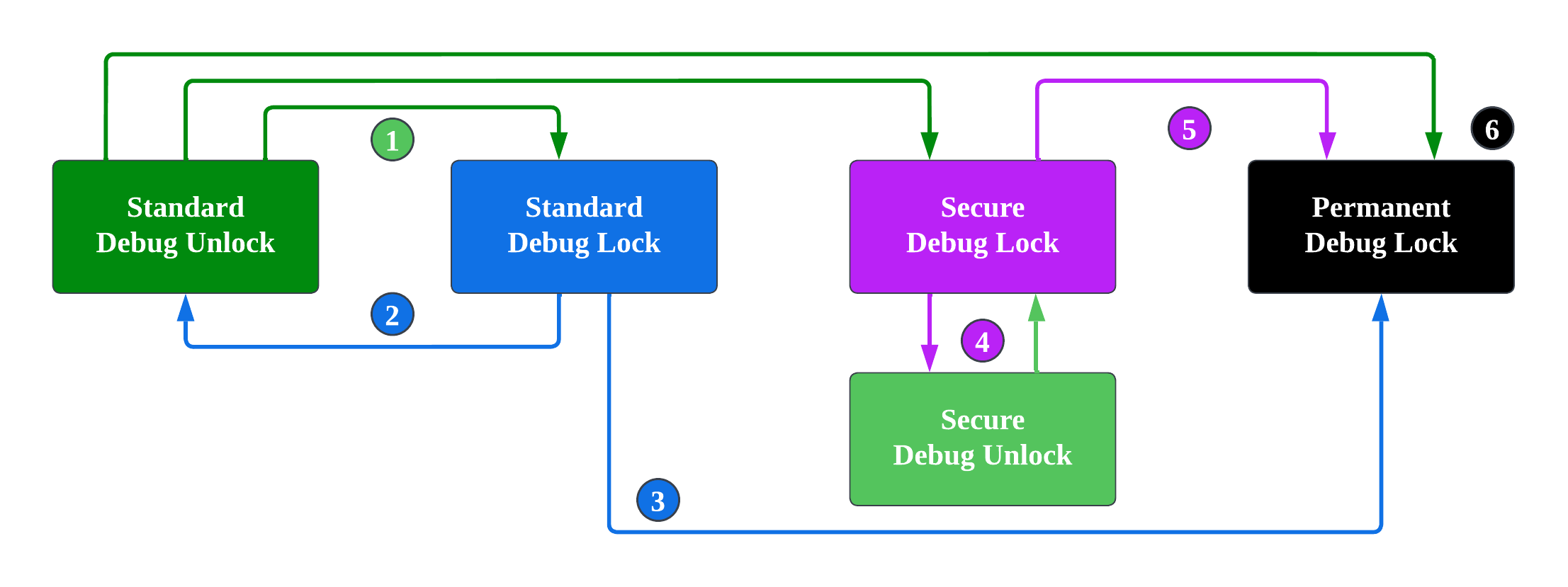

Standard debug unlock can transit to any debug lock state.
Standard debug lock can revert to standard debug unlock via an Erase Device command (erase the main flash and RAM). After the device is reset, debug port remains unlocked until it is explicitly locked again.
Standard debug lock can transit to permanent debug lock by disabling the Device Erase property but cannot transit to secure debug lock.
Secure debug lock can use Debug Unlock Token to temporary transit to secure debug unlock, which does not erase the main flash and RAM but enables debug operations. The device reverts to the secure debug lock through a power-on or pin reset.
Secure debug lock can transit to permanent debug lock by disabling the Secure Debug property but cannot transit to standard debug lock.
Permanent debug lock is a terminal state and cannot transit to any debug lock or unlock state.
Debug Lock Command Reference#
The commands for debug lock are described in the following table.
| DCI Command (1) | Mailbox (SE Manager) API (2) | Description | Availability |
|---|---|---|---|
Apply Lock | sl_se_apply_debug_lock | Enables the debug lock for the part. | While debug is unlocked. |
Read Lock Status | sl_se_get_debug_lock_status | Returns the current debug lock status and configuration. | Always. |
Disable Device Erase | sl_se_disable_device_erase | Disables the Erase Device command. This command does not lock the debug interface to the part, but it is an IRREVERSIBLE action for the part. | Always. |
Disable Secure Debug | sl_se_disable_secure_debug | Disables the secure debug functionality that can be used to open a locked debug port. | While secure debug is enabled. |
Enable Secure Debug | sl_se_enable_secure_debug | Enables the secure debug functionality that can be used to open a locked debug port. | While debug is unlocked and Public Command Key is uploaded. |
Set debug options | sl_se_set_debug_options | Configures the TrustZone access permissions of the debug interface. (3) | While debug is unlocked. |
Init Pub Key | sl_se_init_otp_key | Used to provision a single public key during device initialization. The public key cannot be changed once written, and the command will be unavailable for that key. | Available once for each key. |
Read Pub Key | sl_se_read_pubkey | Reads the stored public key. | Always. |
Get Challenge | sl_se_roll_challenge | Used to roll the current challenge value (16 bytes) to revoke secure debug access. (4) | While Public Command Key is uploaded. |
Notes:
Performing these commands over DCI is implemented in Simplicity Studio and Simplicity Commander.
The
sl_se_apply_debug_lock,sl_se_get_debug_lock_status,sl_se_init_otp_key, andsl_se_read_pubkeyare available on all Series 2 devices. Other APIs are only available on HSE devices. The SE Manager API document can be found at https://docs.silabs.com/gecko-platform/latest/service/api/group-sl-se-manager.For more information about debug options, see TrustZone Debug Authentication.
A new challenge will only be generated if the current one has been successfully used at least once.
