Supported Protocols#
The SiWN917 supports the following protocols:
User Datagram Protocol (UDP)
Transmission Control Protocol (TCP)
Transport Layer Security (TLS)
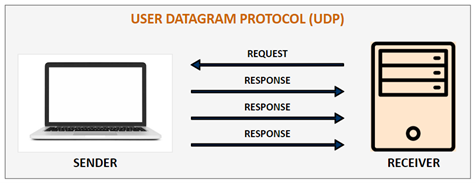
User Datagram Protocol (UDP)#
UDP is a simple, connectionless internet protocol where error-checking and recovery services are not required. It is a lightweight protocol with no support for handshaking, ordering, error recovery etc., and is usually used in protocols that stream music or video. When data transfer is over the internet, packets may be routed through dozens of intermediate nodes as they are sent across the world. Some routers may drop some packets if there is congestion. That is the reason why TCP provides an ACK and retry mechanism. If data is to be sent to a nearby device (local network), then UDP is perfectly reliable. Many implementations of sensor data transfer to a local server could use UDP for simplicity and power savings.
UDP is a preferred protocol where reliability can be traded-off for low end-to-end delay experienced by the users. With UDP, there is no overhead for opening a connection, maintaining a connection, or terminating a connection. Data is continuously sent to the recipient, whether they receive it or not.

UDP Tx#
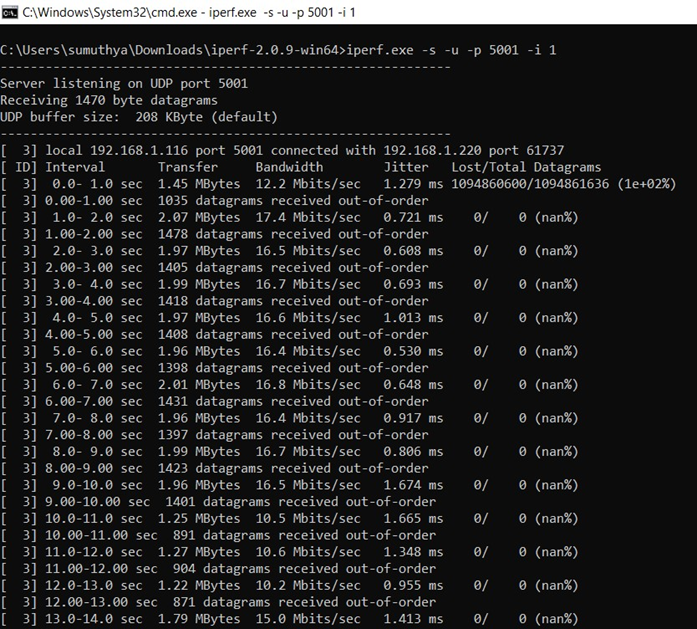
To measure UDP Tx throughput, configure the SiWN917 as a UDP client 



C:\> iperf.exe -s -u -p <SERVER_PORT> -i 1
For example: C:\> iperf.exe -s -u -p 5001 -i 1Note: Refer to wlan_throughput example readme for setup details and other information.
Below iPerf image is for reference. For the expected throughputs, refer to Table Test Results.

UDP Rx#
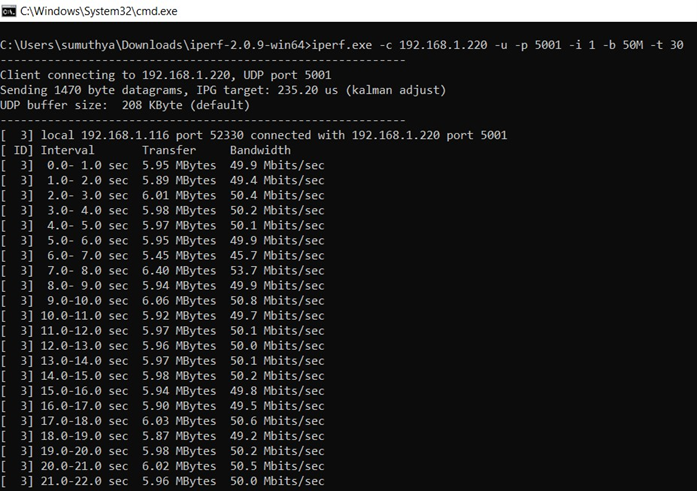
To measure UDP Rx throughput, configure the SiWN917 as a UDP server 



C:\> iperf.exe -c <Module_IP> -u -p <Module_Port> -i 1 -b <Bandwidth> -t <time interval in seconds>
For example: C:\> iperf.exe -c 192.168.1.220 -u -p 5001 -i 1 -b 50M -t 30
Below is the iPerf image for reference:

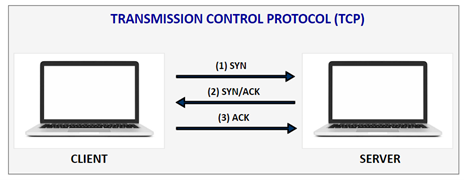
Transmission Control Protocol (TCP)#
TCP is connection-oriented, meaning once a connection has been established, data can be transmitted in two directions. TCP has built-in systems to check for errors and to guarantee data will be delivered in the order it was sent, making it the perfect protocol for transferring information like still images, data files, and web pages.
TCP throughput is the rate at which the data is successfully delivered over a TCP connection. It is an important metric to measure the quality of a network connection. TCP protocol integrates a mechanism that checks that all packets are correctly delivered. This mechanism is called acknowledgment, it consists of having the receiver transmit a specific packet or flag to the sender to confirm the proper reception of a packet.

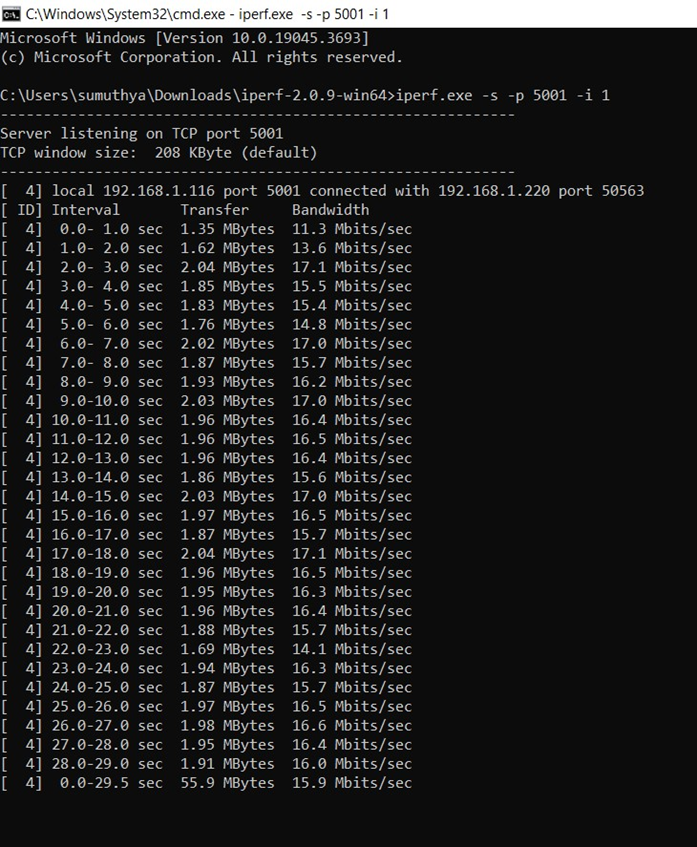
TCP Tx#
To measure TCP Tx throughput, configure the SiWN917 as a TCP client 



C:\> iperf.exe -s -p <SERVER_PORT> -i 1
For example: C:\> iperf.exe -s -p 5001 -i 1
Below is the iPerf image for reference:

TCP Rx#
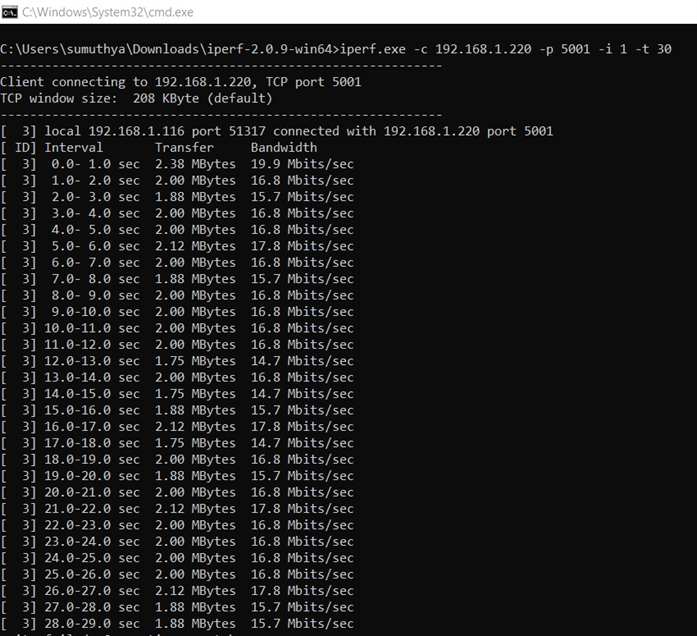
To measure TCP Rx throughput, configure the SiWN917 as a TCP server 



C:\> iperf.exe -c <Module_IP> -p <Module_Port> -i 1 -t <time interval in sec>
For example: C:\> iperf.exe -c 192.168.1.220 -p 5001 -i 1 -t 30
Below is the iPerf image for reference:

Transport Layer Security (TLS)#
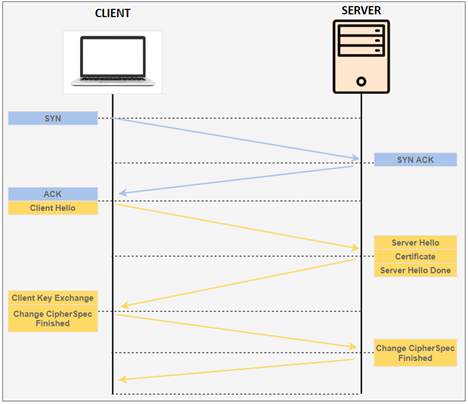
SSL (Secure Sockets Layer) and its successor, Transport Layer Security, or TLS is a widely adopted security protocol designed to facilitate privacy and data security for communication over the Internet. A primary use case of TLS is encrypting the communication between web applications and servers. The three main components to what the TLS protocol accomplishes are encryption, authentication, and integrity.
In order to provide a high degree of privacy, TLS encrypts data that is transmitted across the web. This means that anyone who tries to intercept this data will only see a garbled mix of characters that is nearly impossible to decrypt. TLS then initiates an authentication process called a handshake between two communicating devices to ensure that both devices are really who they claim to be. And then it digitally signs data in order to provide data integrity, verifying that the data is not tampered with before reaching its intended recipient.

TLS Tx#
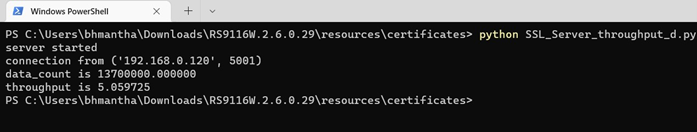

TLS Rx#

Note: All the throughput numbers have been measured in an RF enclosure by running iPerf at the remote peer. Throughput numbers might vary depending on the environment and the wireless traffic on air. It would also differ based on the host interface speeds, host processor capabilities (CPU frequency, RAM, etc.), wireless medium, physical obstacles, distance, etc. Make sure the AP and Server running in PC are connected over ETHERNET cable as it is generally defined as the maximum bandwidth without any packet loss. The SPI clock configurations may be changed depending on the MCU. For configurations, refer to the data sheet of the respective MCU.
