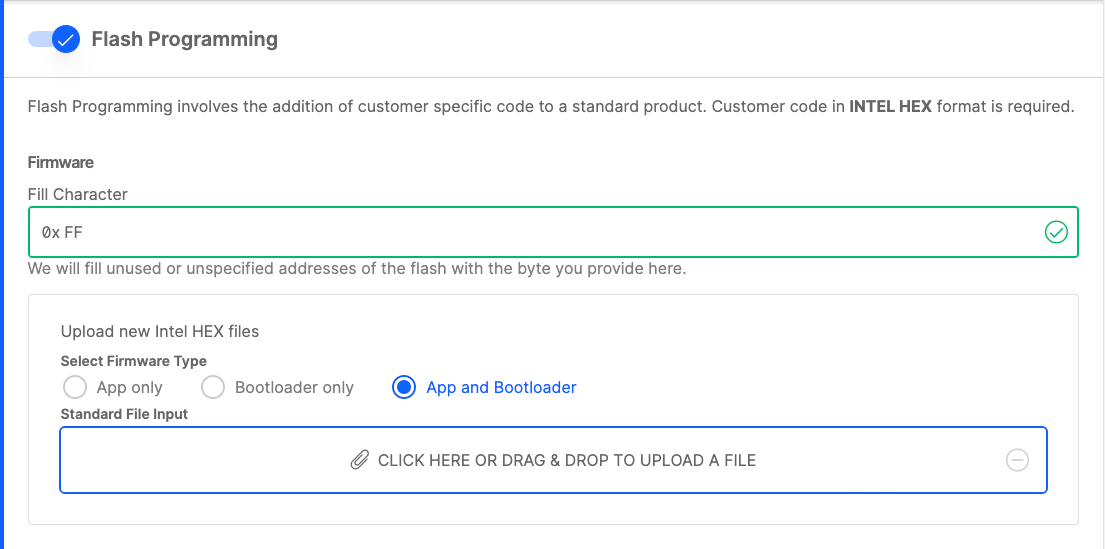
Secure Boot with RTSL Settings#
Secure Boot with RTSL is a security setting available to Silicon Labs’ Series 2 devices that is used to validate the integrity and authenticity of each piece of firmware before the firmware is allowed to run on these devices. Setting up a full root of trust includes enabling secure boot settings in the device’s OTP as well as in the user-generated bootloader. The setting stored in device OTP will enforce the first stage bootloader in the Secure Engine to perform a signature check on the second stage bootloader, which is generated and signed by a user. The next link in the chain is established by enabling secure boot in the second stage bootloader, which will enforce a check on the application image signature.
In CPMS, you can configure the OTP settings for secure boot quickly and easily. These OTP setting are irreversible, so it is recommended to read about each setting in detail before making selections. The OTP settings for Secure Boot with RTSL are the enable bit, Certificates required bit, Anti-Rollback enable bit, and flash page locking settings. Each of these settings is covered in detail in AN1218: Series 2 Secure Boot with RTSL. Once these settings are selected, CPMS will prompt you to provide a secure boot key, also known as a public sign key. This key will be used to sign the firmware to be verified during the secure boot process. For more information on the public sign key, see Secure Boot Key.
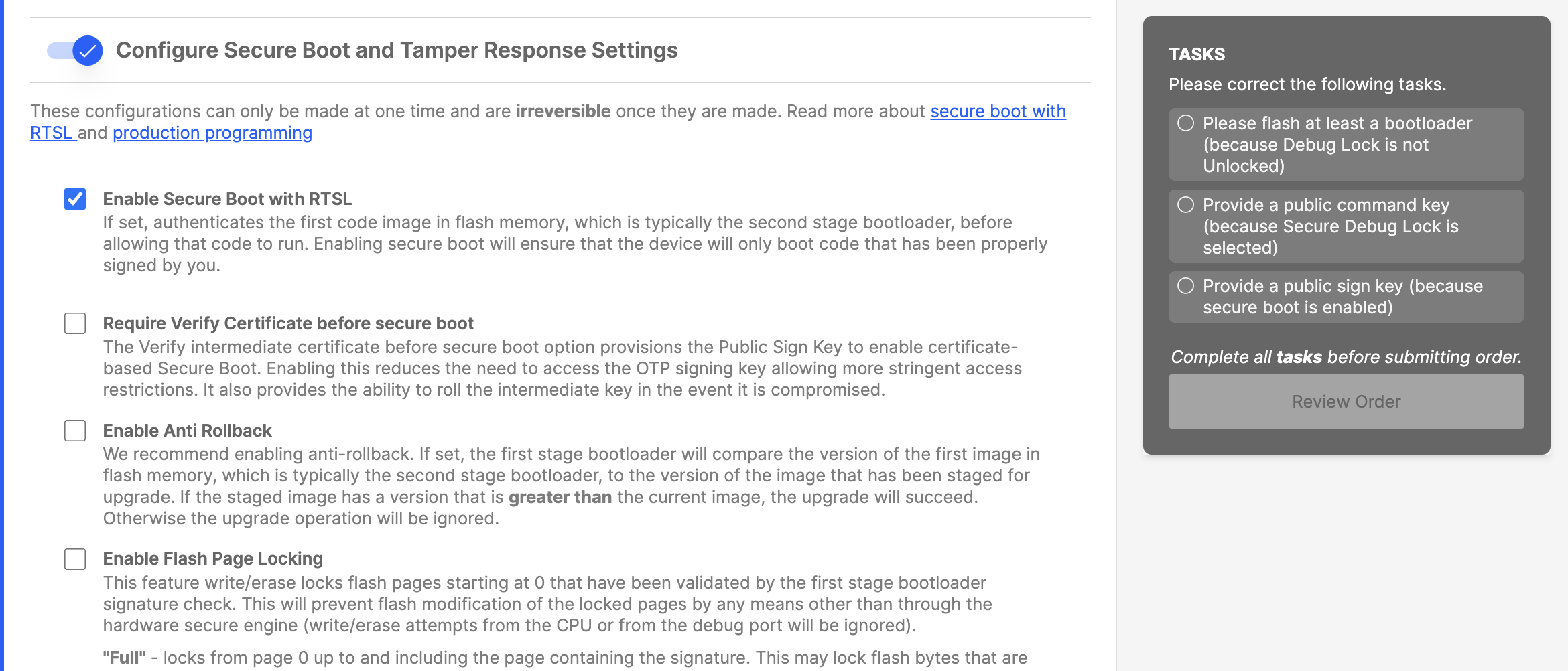

As mentioned previously, to establish the full root of trust for secure boot, secure boot must also be enabled in the bootloader that is uploaded as part of the firmware programming to CPMS. If the OTP setting for secure boot with RTSL was enabled, and the secure boot setting was not enabled in the bootloader, no signature check would be performed on the application image; only a signature check would be performed on the bootloader image. It is recommended to establish a full root of trust to narrow the attack surface of the device. Refer to Generating the Bootloader for instructions on creating a bootloader project with secure boot enabled.
Enabling Secure Boot with RTSL on a VSE Device#
A few extra steps are required to establish a full root of trust when enabling secure boot on a Virtual SE (VSE) device in CPMS. As outlined previously, the secure boot settings in OTP will need to be enabled and a public signing key should be uploaded to CPMS as the first steps to enable secure boot. This public signing key will be provisioned in the device’s OTP memory by CPMS and will be used by the device to verify the signature on the second stage bootloader. For the second stage bootloader to verify the signature on the application on a VSE part, the bootloader will use the public signing key stored in the top page of main flash. Refer to Section 3.2.1 of AN1218 for more information on enabling secure boot with RTSL on a VSE device.
Follow the steps outlined in this section to place the public signing key in flash using a token file.
When creating a public and private signing key pair for secure boot, use the
--tokenfileflag to write the public signing key to the token file. Refer to Section 6.18.3 of UG162 for more information on this command.commander util genkey --type ecc-p256 --privkey sign_privkey.pem --pubkey sign_pubkey.pem --tokenfile sign_pubkey.txtFlash the token file to the device by running the
flashcommand. Refer to Section 6.1.6 of UG162 for more information on this command.commander flash --tokenfile sign_pubkey.txtOnce the token file is flashed to the device, the signed bootloader and application images should be flashed to the device using the same command listed in step 2. To generate and sign a bootloader and application image, follow the steps listed in Section 3.1.2 and 3.1.3.
Dump the flash contents (which contains the token file, signed bootloader, and signed application firmware) to a hex file using the
readmemcommand. Refer to section 6.3.2 of UG162 for more information.commander readmem --region @mainflash --outfile all.hexUpload the file all.hex to CPMS using the App and Bootloader selection in the Flash Programming section. As mentioned, this hex image should contain the token file, signed bootloader, and signed application. This will establish a full root of trust on the VSE device, ensuring that only authentic firmware can run on the device.