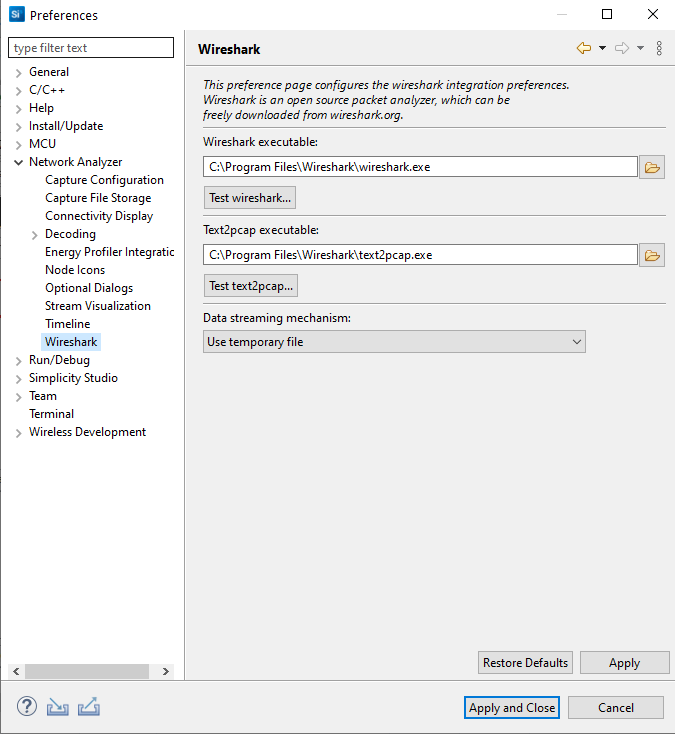
Network Analyzer Preferences#
To access Network Analyzer preferences, select Window > Preferences > Network Analyzer. The preferences you set apply to all capture sessions. Network Analyzer saves your preferences and uses them each time Network Analyzer restarts. Preference categories include:
Stream Visualization (deprecated function)
Capture Configuration Preferences#
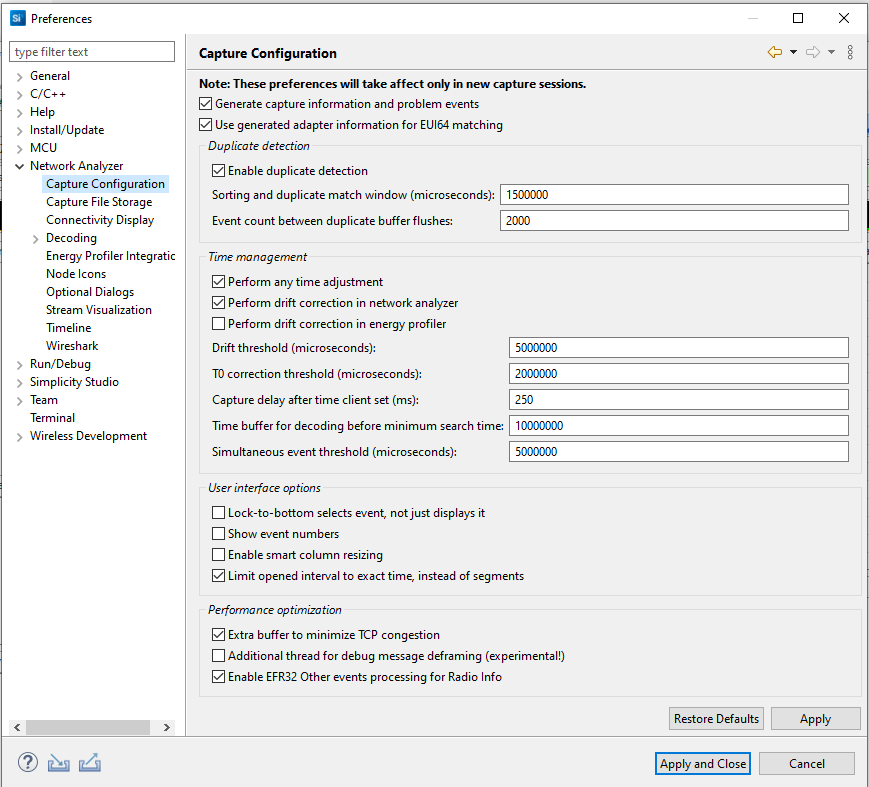

These preferences offer general, time management, and user interface configuration options. Changes take effect in the next new capture session. Some options are:
Sorting and duplicate match window: Specifies in microseconds a time span in which duplicate packets can be detected. If identical packets arrive within the specified time span, Network Analyzer detects the duplication and allows only one to display.
Perform drift correction in network Analyzer: Allows drift for autocorrection.
Drift Threshold: Specifies the amount of time-drift that Network Analyzer will tolerate between the absolute PC clock and the adapter clocks before it resets its "time-correction" factor. In most situations you should not change this value. In a typical situation, adapter clocks are more precise than PC clocks, but they do not provide absolute time, just relative time against an arbitrary reference.
Capture File Storage Preferences#
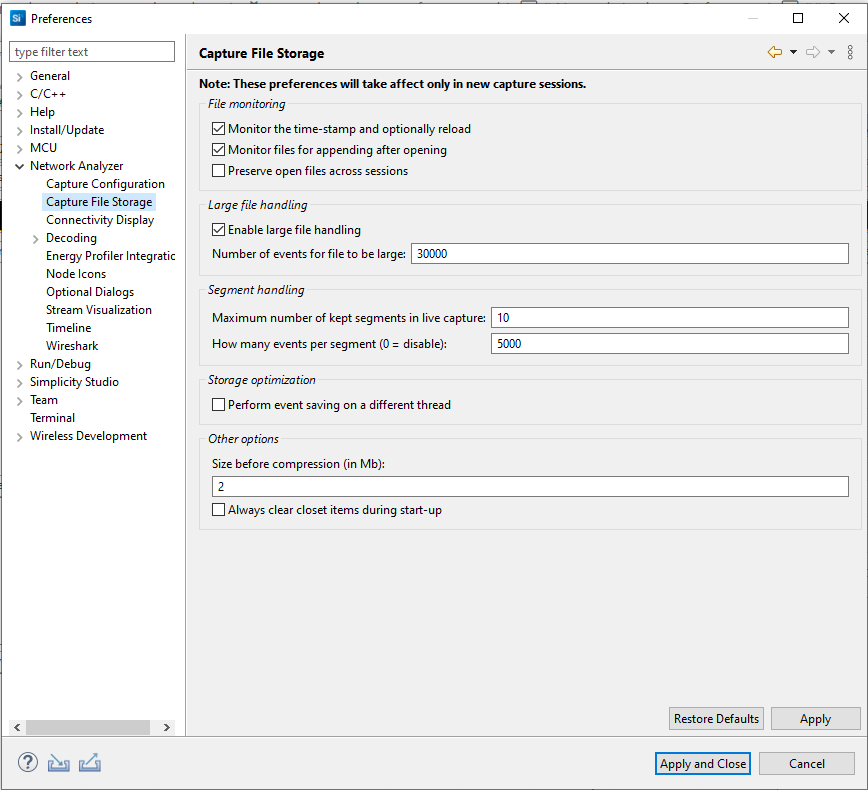

These preferences determine, among other things, what is considered a large file, which in turn determines the default editor used. Changes take effect in the next new capture session. Some of the options are:
Monitor the timestamp and optionally reload: Monitors whether the file has changed on the disk, and prompts to reload if so.
Monitor files for appending after opening: Enables Network Analyzer to detect new packet data appended by an external program to an open session file, and read it in for display.
Preserve open files across sessions: Instructs Network Analyzer to automatically reopen files from previous session
Enable large file handling: Enables Network Analyzer to handle large files in the Large File Editor. Files are considered large if they contain more events than the number entered in "Number of events for a file to be large."
Connectivity Display Preferences#
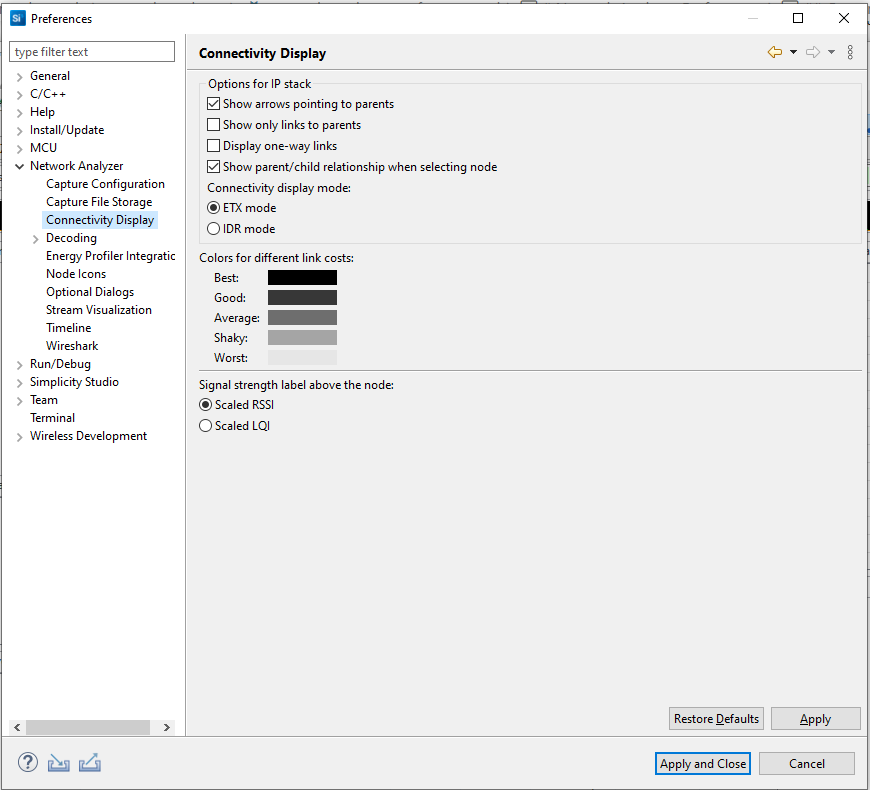

These preferences customize how device connectivity is displayed.
Decoding Preferences#
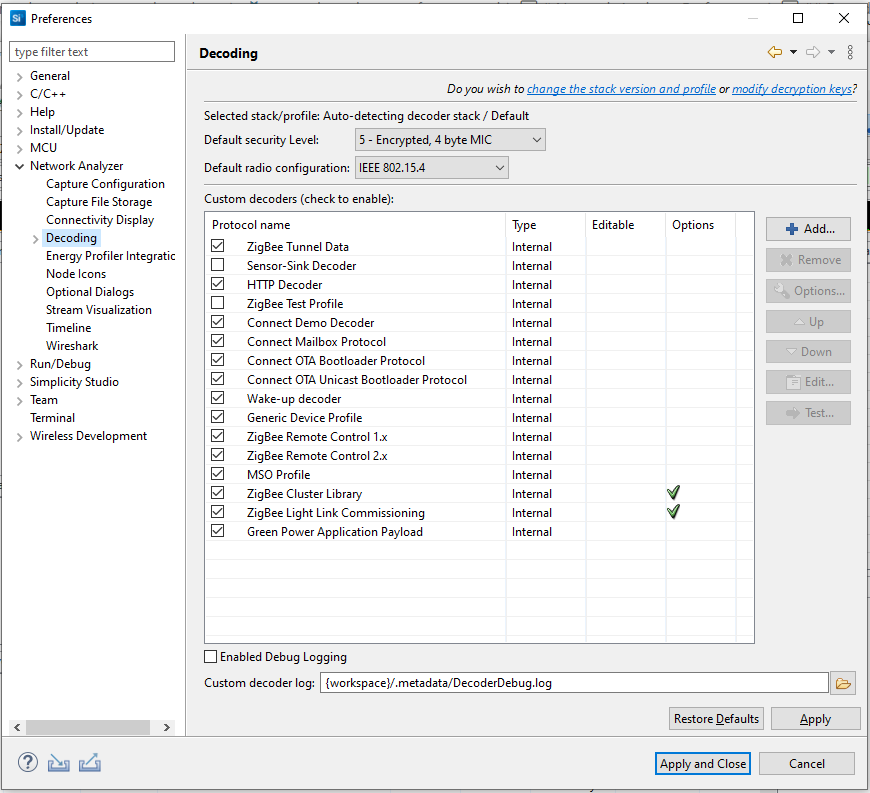

The Decoding preferences group affect how decoding is handled. Changes take effect in the next new capture session. On the Decoding dialog, some options are:
Selected stack: The stack selected for decoding newly captured data. Links allow you to make changes in other preference interfaces. This setting has no effect on a previously captured trace. The decoding stack for a trace file is stored in the file itself.
Security level: The security level set for the MAC and network layers. Valid values include 1 through 5.
Security Keys#
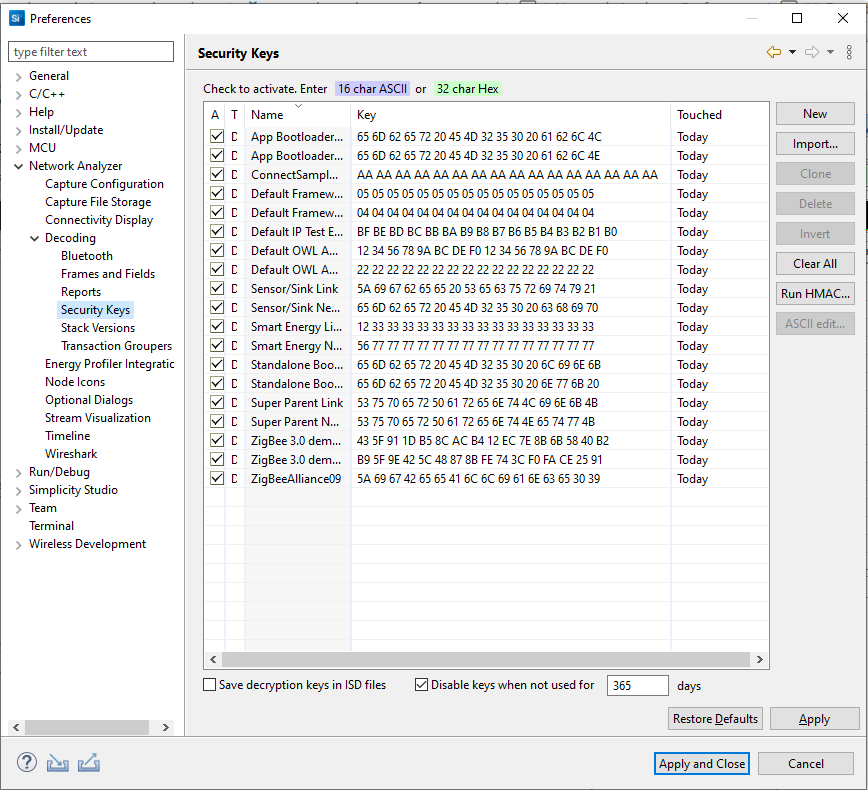

Specifies the security decryption keys. To enable a key, select the Decryption key checkbox. To edit a key, select its name or key values. All enabled decryption keys are run against each incoming packet until one is successful. Successful keys are automatically moved to the top of the key list to improve performance. Decryption keys can also be obtained from network traffic for future use.
Buttons on the right of the dialog provide the following features:
New: Creates a new key for editing.
Import: Opens a dialog from which you can import a key file.
Clone: Creates a copy of the currently selected key.
Delete: Removes the currently selected key.
Invert swaps the order of the key values.
Clear All: Removes all security keys.
Run HMAC: Opens a dialog that allows you to manually calculate the HMAC authenticated key from trust key and IEEE EUI64 address.
ASCII edit...: Converts a human-readable ASCII string into a binary security key.
The checkboxes at the bottom of the keys list provide the following options:
Save decryption keys in ISD files (unchecked by default): Saves the security keys that you have specified into the capture file along with your traffic. Note: If you are sharing the Network Analyzer file with users who have a right to know your key, this may make the opening of the file easier for them, as they will not have to separately enter the key. However, by doing this, you create a security risk. Never enable this option, if your keys must remain secure and known to you only.
Disable keys when not used for n days (checked by default): You can configure the number of days unused keys should be kept.
Stack Versions#
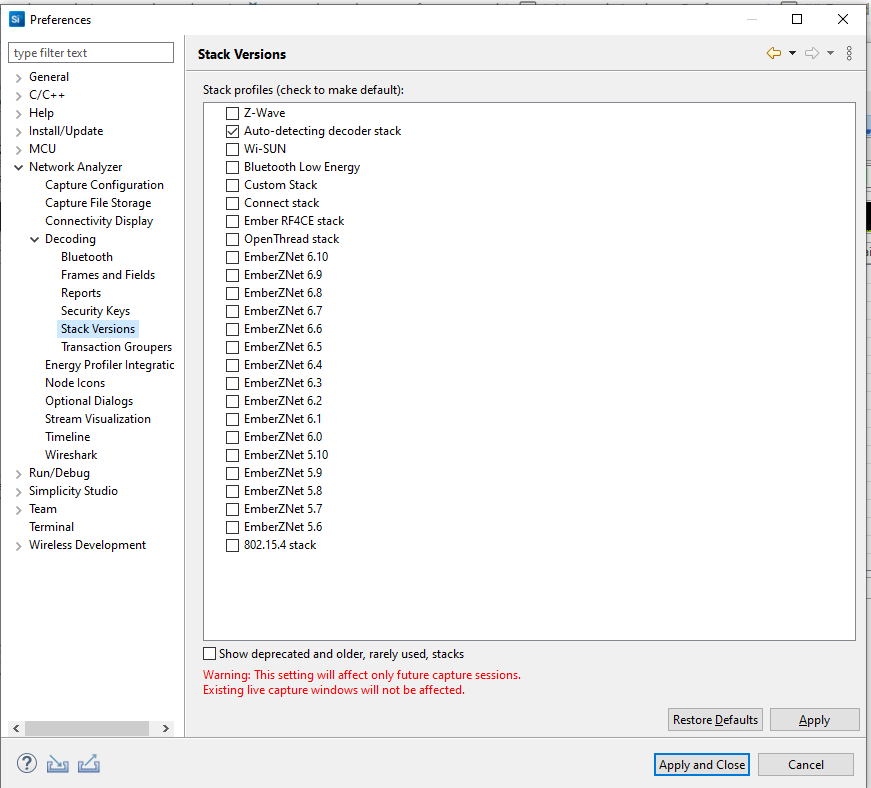

A list of profiles representing Gecko SDK Suite stack versions. Check the stack that is deployed on the network you are using. If you are working with Dynamic Multiprotocol projects, select 'Auto-detecting decoder stack'.
Transaction Groupers#
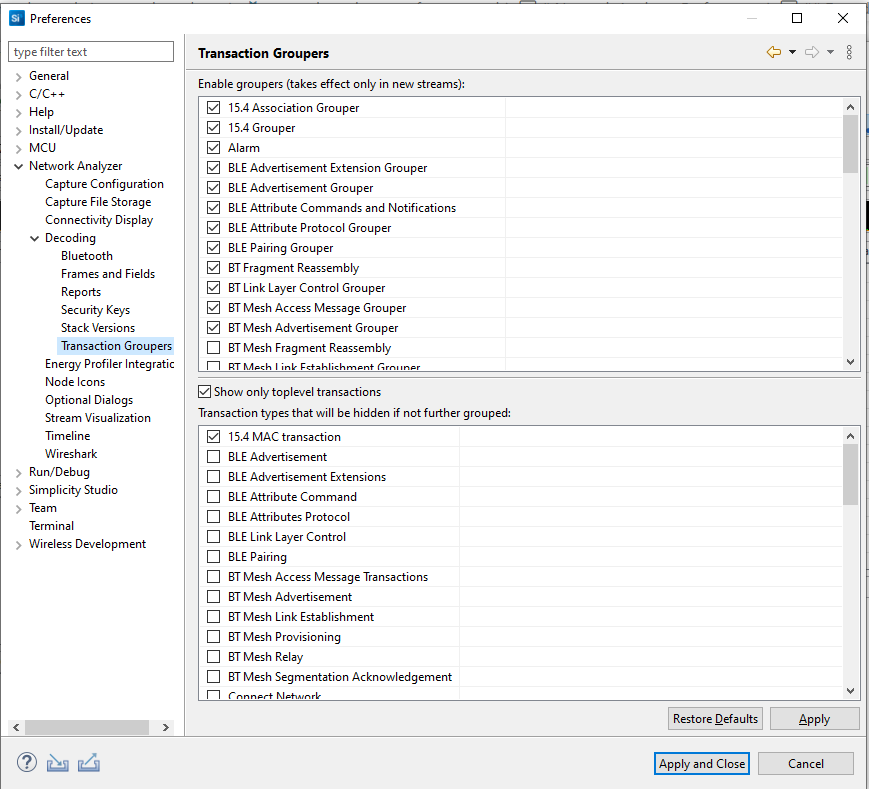

A table of all the groupers loaded into Network Analyzer. Transaction groupers are responsible for making transactional sense out of a trace of network data. Groupers watch for batches of events and record them as a transaction.
Energy Profiler Integration Preferences#
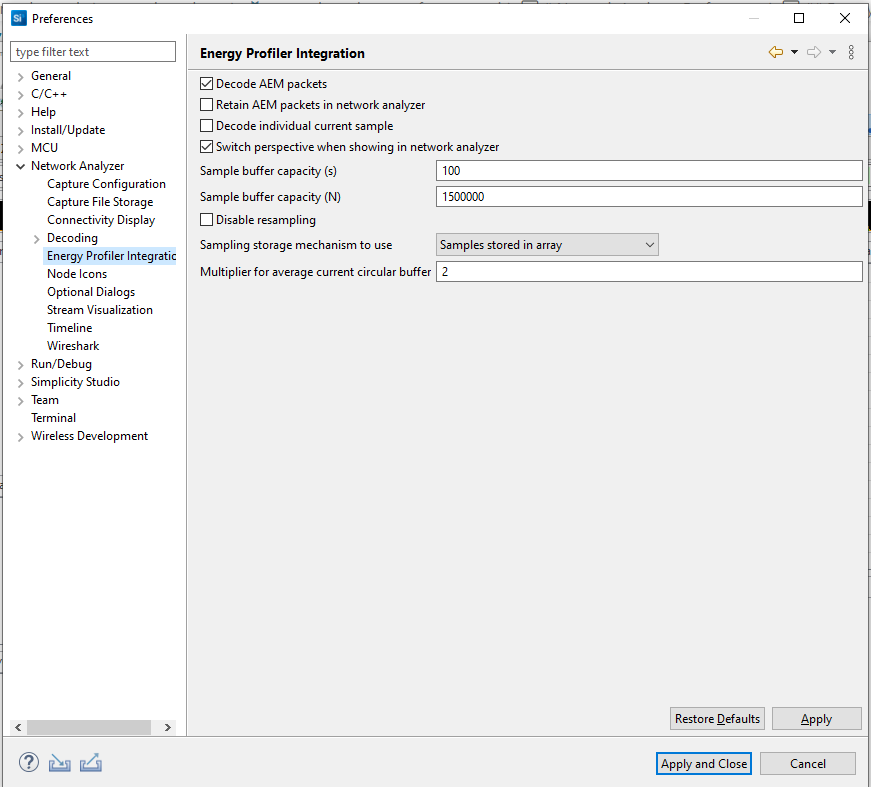

See Energy Profiler and Network Analyzer in the Energy Profiler section for more information about using the two tools together and the effect of these preferences.
Node Icon Preferences#
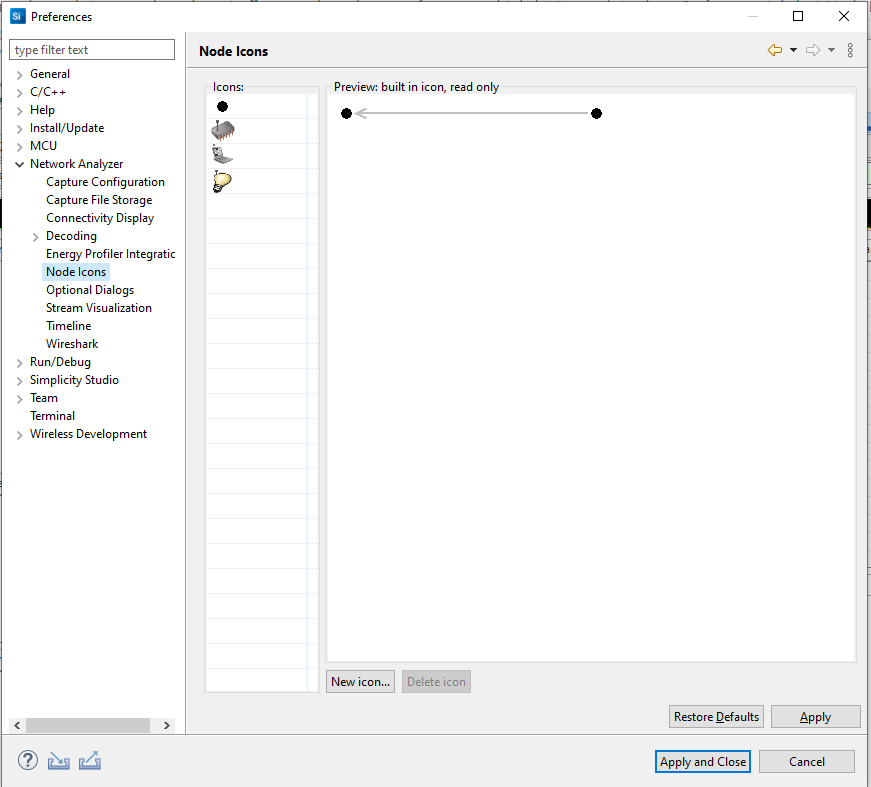

Network Analyzer provides several predefined icons. The Node Icons dialog displays all icons that are available for customizing display of nodes in the map pane. You can also add icons of your own.
Optional Dialog Preferences#
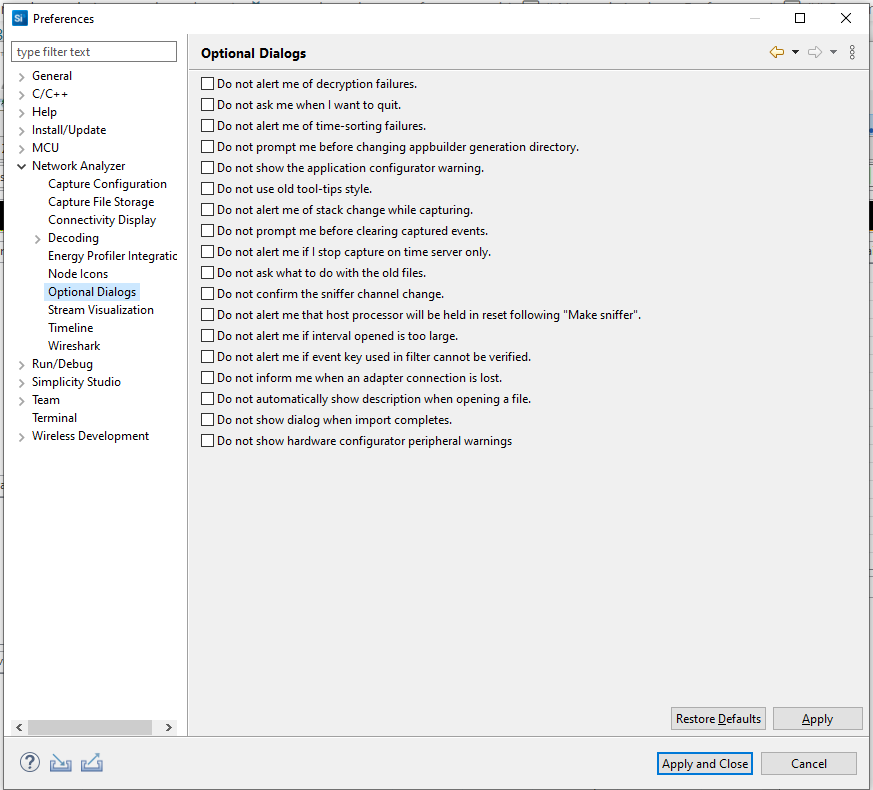

Some dialogs can be turned off if you prefer not to interact with them.
Timeline Preferences#
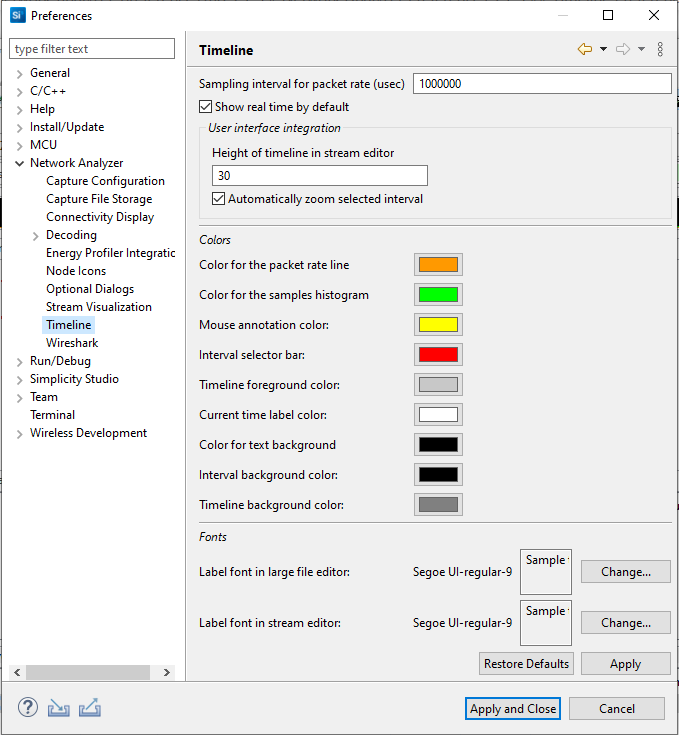

Among other options, you can choose the colors and fonts for features of the Timeline.
Wireshark Preferences#
If you are using the Wireshark open source packet analyzer, these options configure the integration.