Secure SPP (Serial Port Profile) over BLE#
Background#
This code example has a related User's Guide, here: Using Bluetooth Security Features
Description#
This code example demonstrates how to build a secure Bluetooth connection between two EFR32 devices and how to implement secure serial communication between them. The example relies on the Serial Port Profile (SPP) over BLE example which implements the serial communication between the two devices. See the SPP example first to understand how it works. This example puts emphasis on the security side.
Just like with SPP over BLE, the client and server roles are combined into one code. Upload the same code to both devices that you want to connect. The roles are configured by holding down either pushbutton at boot time. Holding down the button makes that device a master (client), which is scanning for other devices that implements the SPP service. If none of the buttons is held down during reset, the device becomes a slave (server) and starts advertising.
When the connection is built and services and characteristics are discovered, the devices have to go through an authentication phase before starting secure data transfer. In this example, I/O capabilities are defined to DisplayYesNo, which ultimately results in a Numeric Comparison pairing method. For details, see the description of Pairing Processes.
During the authentication phase, the devices have to confirm that they have successfully built a secure connection by showing passkeys on both devices. If the passkeys match and both devices confirm it, they are bonded (paired). If the devices were already bonded when they connected, the authentication is not needed again and the secure connection is automatically built using the long term key stored in the flash.
Bonding information including the long term key and other information persists over reset. To test the authentication repeatedly, implement a call to sm_delete_bondings with a trigger of your choice. Another option is to use Simplicity Commander tool to erase the devices' flash.
Setting up#
Create a new SoC-Empty project for your device.
Copy the attached files into it (overwriting existing ones).
Import gatt.xml into the GATT Configurator.
Press Save and then Generate in the GATT Configurator.
Enable debug printing by setting DEBUG_LEVEL to 1 in app.h.
Build and flash the project to two devices.
Usage#
Open a terminal program (e.g., TeraTerm) and connect to both devices to see the logs.
Press PB0 or PB1 on one of the devices while resetting it to put it into client mode.
Simply reset the other device to put it into server mode.
After the first boot, the authentication phase requires confirmation that the passkeys displayed on the two devices match. To confirm, send a 'y' or 'Y' character with the terminal. To decline send 'n' or 'N'.
After the authentication phase, use the application to send characters from one device to the other just like with the SPP over BLE example.
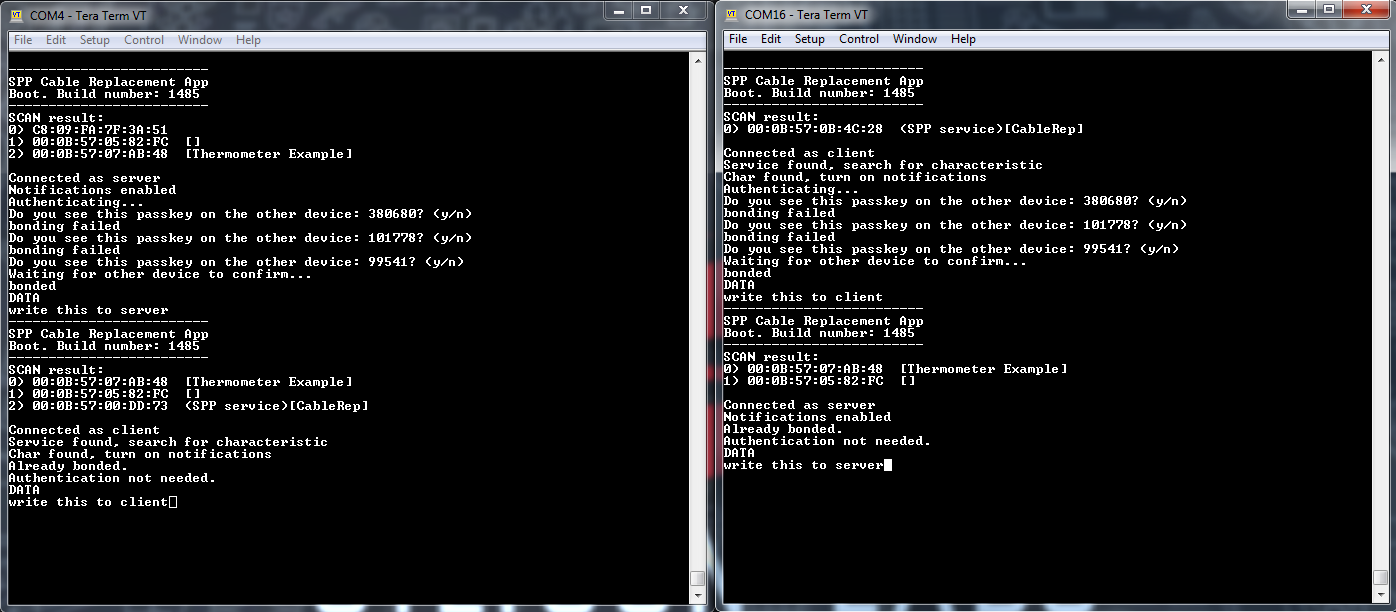

Reboot the devices and check if the secure connection is built automatically.
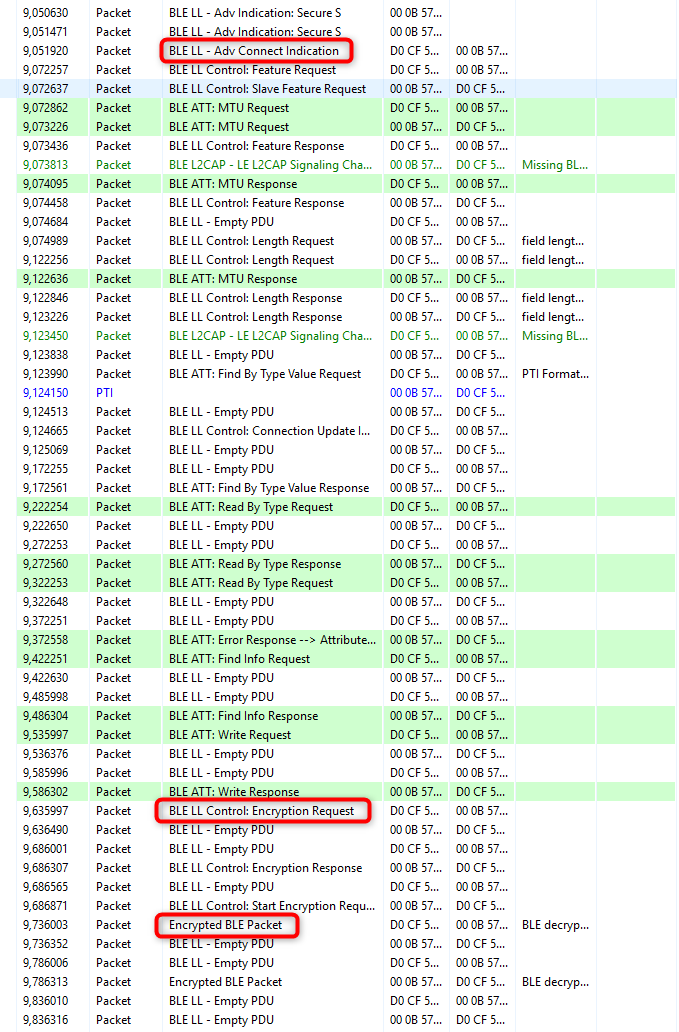
Open the Network Analyzer, connect to one of the devices, and check its traffic. You should see encrypted content.
Note: to get a proper log, Network Analyzer needs to observe the connection from the very beginning. Hence, after connecting to your device, reset it, and let the Network Analyzer observe the connection establishment process.