Introduction#
Execute in Place (XIP) is a technology used in computing to run software directly from long-term storage, such as a ROM or Flash memory, without requiring that the software be copied into RAM before execution. By eliminating RAM usage, an embedded system with XiP support can reduce memory requirements and die cost can improve power consumption in IoT devices. While XiP offers enhanced security, it also has drawbacks in terms of execution speed that must be considered during system design. The encryption of flash memory content requires additional CPU cycles for decryption, leading to a decrease in execution speed by 25 to 43 %.
In SiWx917 devices, Execute in Place (XiP) refers to loading instructions from Flash memory directly via the Quad-Serial Peripheral Interface (Quad SPI). Additionally, SiWx917 has integrated hardware AES accelerators that can decrypt XiP instructions in real-time without the executing program being aware of the decryption process. Quad SPI is used to improve speed of execution, while an on-the-fly hardware AES engine improves firmware confidentiality. SiWx917 supports encrypted and unencrypted XiP on both the NWP and M4 cores in all operating modes except Radio Co-Processor (RCP) mode. Additionally, XiP can be configured independently per-core.
Some AI/ML algorithms or applications which drive displays using Frame buffers require huge RAM. Internal RAM may not be sufficient in such cases, so an external PSRAM of 2, 4, 8, or 16 MB can be added. If these contents are in plain form bad actors can easily tamper with the contents of external RAM. Additionally, programs can also be configured to be executed directly from PSRAM. So, to secure the contents of PSRAM encrypted XIP functionality can be extended to PSRAM.
As illustrated in the diagram below, M4 accesses both FLASH and PSRAM via QSPI. The NWP accesses the contents through a secure AHB bridge. The QSPI controller retrieves contents from external memory, decrypts them, and places them in cache memory.
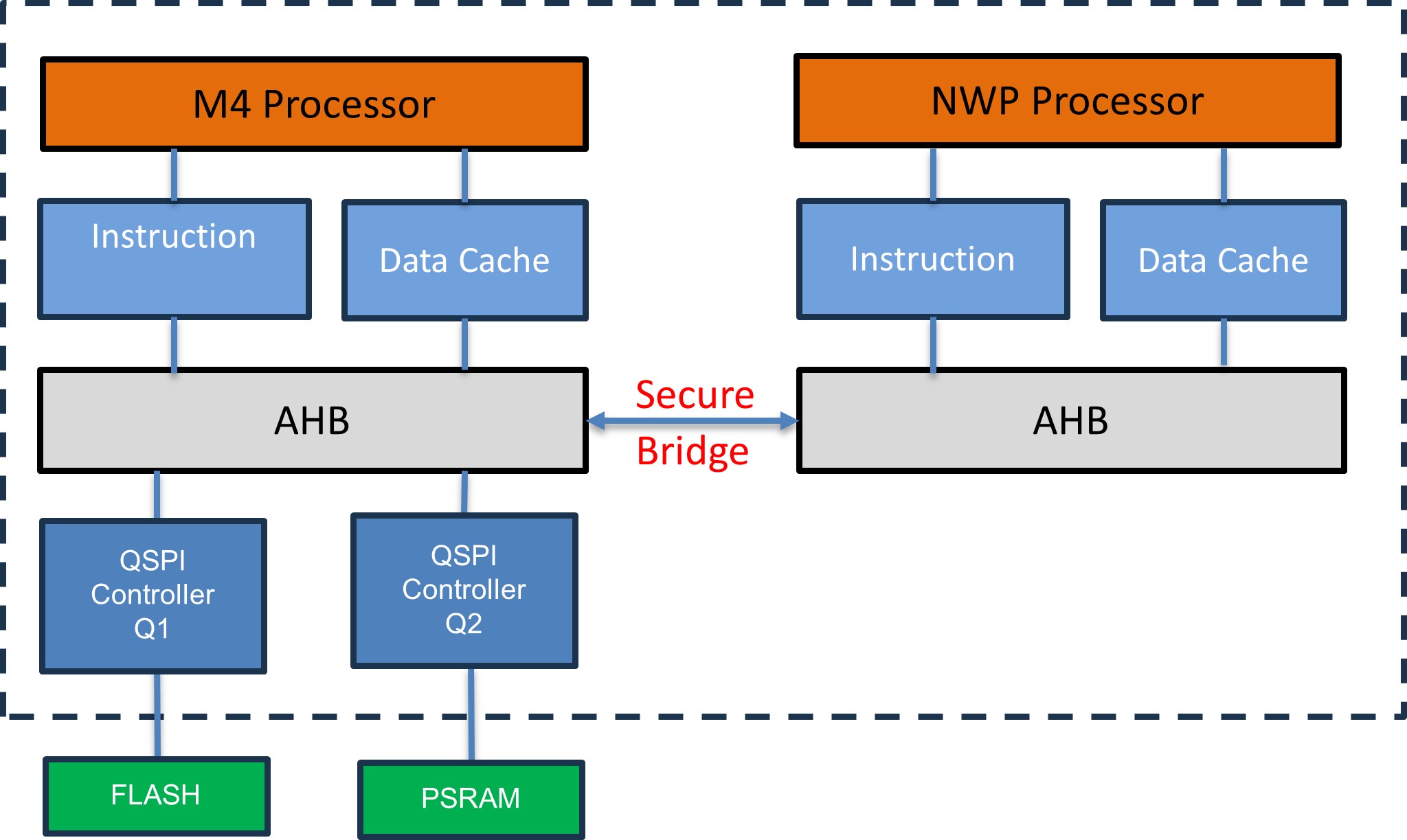

For PSRAM, only AES-CTR mode with 128-bit and 256-bit key sizes is supported. Whereas for FLASH both AES-XTS and AES-CTR modes with 128-bit and 256-bit key sizes are supported.
Note: Entire contents of FLASH/PSRAM contents are not encrypted. Areas that need to be encrypted are configurable by application program.
QSPI Overview#
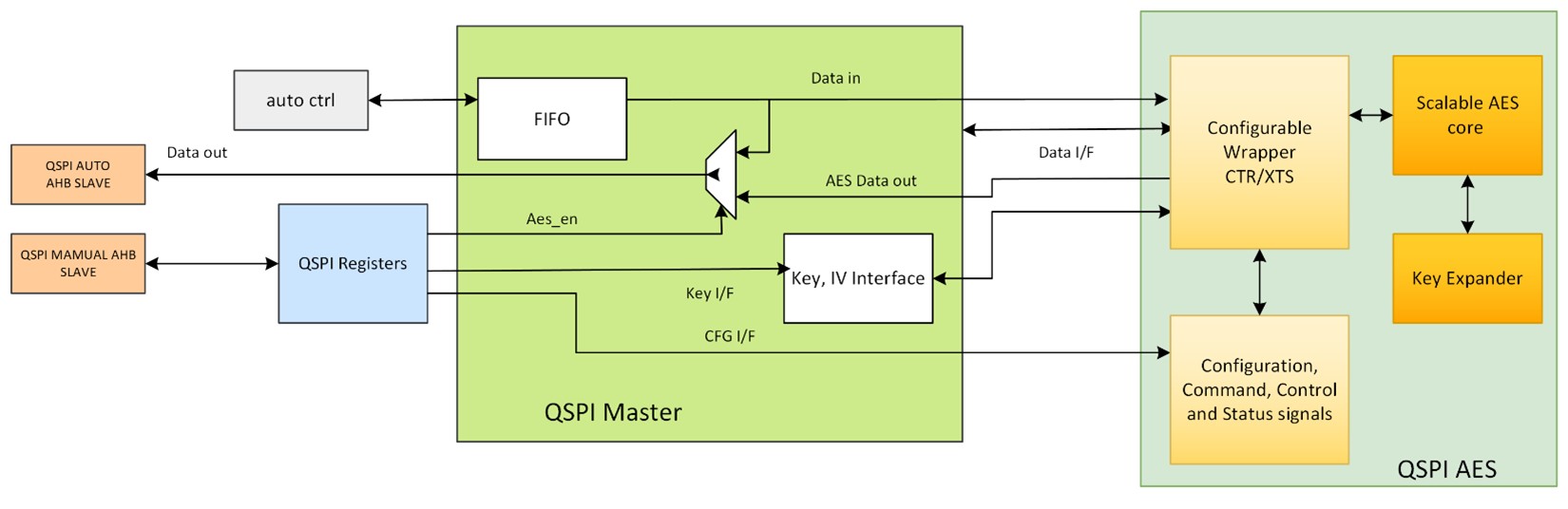
Encrypted XiP is achieved on the SiWx917 through its integrated Quad SPI (QSPI) and AES engine components. The AES engine is designed to be compliant with NIST FIPS 197 and supports two ciphering modes from NIST SP 800-38: non-chaining CTR mode and AES-XTS.

PUF Initialization#
Both cores of the SiWx917 can be independently configured for XiP with or without encryption. To enable encrypted XiP the SiWx917 PUF token must be initialized, and a corresponding encrypted XiP intrinsic key needs to be provisioned for the given core being placed into encrypted XiP mode.
Without provisioning the PUF, intrinsic XiP encryption keys will not be generated and XiP will not function. For more information configuring the PUF and provisioning device intrinsic keys, see Activation Code Generation for PUF Block of UG574 – SiWx917 SoC Manufacturing Utility Users Guide – which contains sample mbr json files for configuring encrypted XiP in both operating modes.
